The U.S. government has demanded that major Internet companies divulge users' stored passwords, according to two industry sources familiar with these orders, which represent an escalation in surveillance techniques that has not previously been disclosed.
If the government is able to determine a person's password, which is typically stored in encrypted form, the credential could be used to log in to an account to peruse confidential correspondence or even impersonate the user. Obtaining it also would aid in deciphering encrypted devices in situations where passwords are reused.
"I've certainly seen them ask for passwords," said one Internet industry source who spoke on condition of anonymity. "We push back."
A second person who has worked at a large Silicon Valley company confirmed that it received legal requests from the federal government for stored passwords. Companies "really heavily scrutinize" these requests, the person said. "There's a lot of 'over my dead body.'"
Some of the government orders demand not only a user's password but also the encryption algorithm and the so-called salt, according to a person familiar with the requests. A salt is a random string of letters or numbers used to make it more difficult to reverse the encryption process and determine the original password. Other orders demand the secret question codes often associated with user accounts.
A Microsoft spokesperson would not say whether the company has received such requests from the government. But when asked whether Microsoft would divulge passwords, salts, or algorithms, the spokesperson replied: "No, we don't, and we can't see a circumstance in which we would provide it."
Google also declined to disclose whether it had received requests for those types of data. But a spokesperson said the company has "never" turned over a user's encrypted password, and that it has a legal team that frequently pushes back against requests that are fishing expeditions or are otherwise problematic. "We take the privacy and security of our users very seriously," the spokesperson said.
A Yahoo spokeswoman would not say whether the company had received such requests. The spokeswoman said: "If we receive a request from law enforcement for a user's password, we deny such requests on the grounds that they would allow overly broad access to our users' private information. If we are required to provide information, we do so only in the strictest interpretation of what is required by law."
Apple, Facebook, AOL, Verizon, AT&T, Time Warner Cable, and Comcast did not respond to queries about whether they have received requests for users' passwords and how they would respond to them.
Richard Lovejoy, a director of the Opera Software subsidiary that operates FastMail, said he doesn't recall receiving any such requests but that the company still has a relatively small number of users compared with its larger rivals. Because of that, he said, "we don't get a high volume" of U.S. government demands.
The FBI declined to comment.
Some details remain unclear, including when the requests began and whether the government demands are always targeted at individuals or seek entire password database dumps. The Patriot Act has been used to demand entire database dumps of phone call logs, and critics have suggested its use is broader. "The authority of the government is essentially limitless" under that law, Sen. Ron Wyden, an Oregon Democrat who serves on the Senate Intelligence committee, said at a Washington event this week.
Large Internet companies have resisted the government's requests by arguing that "you don't have the right to operate the account as a person," according to a person familiar with the issue. "I don't know what happens when the government goes to smaller providers and demands user passwords," the person said.
An attorney who represents Internet companies said he has not fielded government password requests, but "we've certainly had reset requests -- if you have the device in your possession, than a password reset is the easier way."
Cracking the codes
Even if the National Security Agency or the FBI successfully obtains an encrypted password, salt, and details about the algorithm used, unearthing a user's original password is hardly guaranteed. The odds of success depend in large part on two factors: the type of algorithm and the complexity of the password.
Algorithms, known as hash functions, that are viewed as suitable for scrambling stored passwords are designed to be difficult to reverse. One popular hash function called MD5, for instance, transforms the phrase "National Security Agency" into this string of seemingly random characters: 84bd1c27b26f7be85b2742817bb8d43b. Computer scientists believe that, if a hash function is well-designed, the original phrase cannot be derived from the output.
But modern computers, especially ones equipped with high-performance video cards, can test passwords scrambled with MD5 and other well-known hash algorithms at the rate of billions a second. One system using 25 Radeon-powered GPUs that was demonstrated at a conference last December tested 348 billion hashes per second, meaning it would crack a 14-character Windows XP password in six minutes.
The best practice among Silicon Valley companies is to adopt far slower hash algorithms -- designed to take a large fraction of a second to scramble a password -- that have been intentionally crafted to make it more difficult and expensive for the NSA and other attackers to test every possible combination.
One popular algorithm, used by Twitter and LinkedIn, is called bcrypt. A 2009 paper (PDF) by computer scientist Colin Percival estimated that it would cost a mere $4 to crack, in an average of one year, an 8-character bcrypt password composed only of letters. To do it in an average of one day, the hardware cost would jump to approximately $1,500.
But if a password of the same length included numbers, asterisks, punctuation marks, and other special characters, the cost-per-year leaps to $130,000. Increasing the length to any 10 characters, Percival estimated in 2009, brings the estimated cracking cost to a staggering $1.2 billion.
As computers have become more powerful, the cost of cracking bcrypt passwords has decreased. "I'd say as a rough ballpark, the current cost would be around 1/20th of the numbers I have in my paper," said Percival, who founded a company called Tarsnap Backup, which offers "online backups for the truly paranoid." Percival added that a government agency would likely use ASICs -- application-specific integrated circuits -- for password cracking because it's "the most cost-efficient -- at large scale -- approach."
While developing Tarsnap, Percival devised an algorithm called scrypt, which he estimates can make the "cost of a hardware brute-force attack" against a hashed password as much as 4,000 times greater than bcrypt.
Bcrypt was introduced (PDF) at a 1999 Usenix conference by Niels Provos, currently a distinguished engineer in Google's infrastructure group, and David Mazières, an associate professor of computer science at Stanford University.
With the computers available today, "bcrypt won't pipeline very well in hardware," Mazières said, so it would "still be very expensive to do widespread cracking."
Even if "the NSA is asking for access to hashed bcrypt passwords," Mazières said, "that doesn't necessarily mean they are cracking them." Easier approaches, he said, include an order to extract them from the server or network when the user logs in -- which has been done before -- or installing a keylogger at the client.
Source:Cnet
ComputerNews
duminică, 28 iulie 2013
Fortune 500 companies give social media a thumbs-up
It appears the world's biggest moneymakers are paying increasing attention to social media.
A new report by the University of Massachusetts Dartmouth takes a look at how often companies on Fortune Magazine's Fortune 500 list are using social-media sites like Facebook, Twitter, Google+, Instagram, YouTube, Foursquare, and Pinterest. And the answer is: a lot.
Of those Fortune 500 companies, 77 percent keep active Twitter accounts, 70 percent have a Facebook page, and 69 percent have YouTube accounts. All these stats are up over last year -- with 4 percent more companies keeping Twitter accounts, 4 percent more having a Facebook page, and 7 percent more on YouTube.
Other social networks aren't as popular with the Fortune 500 companies, but they still have some presence. According to the report, 35 percent of companies have an active Google+ account. Of the 500 companies, 44 are on Instagram, 44 are on Foursquare, and 45 have Pinterest accounts.
"Due to the hugely influential role that these companies play in the business world, studying their adoption and use of social-media tools offers important insights into the future of commerce," the report reads. "These corporations provide a look at emergent social-media trends among America's most successful companies."
Not surprisingly, the company that tops the list in social-media activity is a social network itself -- Facebook. Ranked 482 on the Fortune 500 list, Facebook has more than 8.5 million Twitter followers and more than 92 million Facebook fans.
Other leading companies on Twitter include Google, Starbucks, and Whole Foods. While popular Facebook companies included Coca-Cola, Walt Disney, and Starbucks. (See graphs below.)
In addition to being more active on social media, Fortune 500 companies are also blogging more. This year, at 34 percent, more companies than ever have a public facing blog. Currently, 171 companies blog, including two of the top five Fortune 500 companies: Walmart and Exxon.
"This is a group that now seems comfortable and even excited with its newfound ability to engage its vendors, partners, customers, and others in ways that could not have been imagined when most of their corporations began," the report reads. "Judging by the increased use of tools, fans, and followers, they are making some very powerful new connections."
Source:Cnet
A new report by the University of Massachusetts Dartmouth takes a look at how often companies on Fortune Magazine's Fortune 500 list are using social-media sites like Facebook, Twitter, Google+, Instagram, YouTube, Foursquare, and Pinterest. And the answer is: a lot.
Of those Fortune 500 companies, 77 percent keep active Twitter accounts, 70 percent have a Facebook page, and 69 percent have YouTube accounts. All these stats are up over last year -- with 4 percent more companies keeping Twitter accounts, 4 percent more having a Facebook page, and 7 percent more on YouTube.
Other social networks aren't as popular with the Fortune 500 companies, but they still have some presence. According to the report, 35 percent of companies have an active Google+ account. Of the 500 companies, 44 are on Instagram, 44 are on Foursquare, and 45 have Pinterest accounts.
"Due to the hugely influential role that these companies play in the business world, studying their adoption and use of social-media tools offers important insights into the future of commerce," the report reads. "These corporations provide a look at emergent social-media trends among America's most successful companies."
Not surprisingly, the company that tops the list in social-media activity is a social network itself -- Facebook. Ranked 482 on the Fortune 500 list, Facebook has more than 8.5 million Twitter followers and more than 92 million Facebook fans.
Other leading companies on Twitter include Google, Starbucks, and Whole Foods. While popular Facebook companies included Coca-Cola, Walt Disney, and Starbucks. (See graphs below.)
In addition to being more active on social media, Fortune 500 companies are also blogging more. This year, at 34 percent, more companies than ever have a public facing blog. Currently, 171 companies blog, including two of the top five Fortune 500 companies: Walmart and Exxon.
"This is a group that now seems comfortable and even excited with its newfound ability to engage its vendors, partners, customers, and others in ways that could not have been imagined when most of their corporations began," the report reads. "Judging by the increased use of tools, fans, and followers, they are making some very powerful new connections."
Source:Cnet
Google doodle honors birthday of biophysicist Rosalind Franklin
Google devoted its doodle on Thursday to mark the 93rd birthday of Rosalind Franklin, a British biophysicist and X-ray crystallographer who made great strides in our understanding of the molecular makeup of DNA and RNA but missed out on the Nobel Prize.
Born in London on July 25, 1920, Franklin showed exceptional scholastic aptitude at an early age. After studying chemistry at Cambridge, Franklin went to work as a research associate at King's College London in the Medical Research Council's Biophysics Unit. During her tenure at King's College, she captured X-ray diffraction images of DNA that led to the discovery of the DNA's double helix. Her data was the basis for a 1953 hypothesis regarding the structure of DNA that led to the 1962 Nobel Prize.
Franklin died of ovarian cancer in 1958 at age 37 and was ineligible for Nobel Prize nomination in 1962. The honor was bestowed on Francis Crick, James Watson, and Maurice Wilkins based on their work contributing to the understanding of nucleic acids and not exclusively for their DNA structure discoveries. However, Crick wrote in 1961 that Franklin's data was "the data we actually used" to formulate their hypothesis on the structure of DNA.
While her exposure to X-ray radiation is sometimes linked to the illness that killed her, other members of her family have died of cancer.
Franklin's studies also contributed to the understanding of the molecular structures of viruses, coal, and graphite.
Born in London on July 25, 1920, Franklin showed exceptional scholastic aptitude at an early age. After studying chemistry at Cambridge, Franklin went to work as a research associate at King's College London in the Medical Research Council's Biophysics Unit. During her tenure at King's College, she captured X-ray diffraction images of DNA that led to the discovery of the DNA's double helix. Her data was the basis for a 1953 hypothesis regarding the structure of DNA that led to the 1962 Nobel Prize.
Franklin died of ovarian cancer in 1958 at age 37 and was ineligible for Nobel Prize nomination in 1962. The honor was bestowed on Francis Crick, James Watson, and Maurice Wilkins based on their work contributing to the understanding of nucleic acids and not exclusively for their DNA structure discoveries. However, Crick wrote in 1961 that Franklin's data was "the data we actually used" to formulate their hypothesis on the structure of DNA.
While her exposure to X-ray radiation is sometimes linked to the illness that killed her, other members of her family have died of cancer.
Franklin's studies also contributed to the understanding of the molecular structures of viruses, coal, and graphite.
marți, 7 mai 2013
AutoIt scripting increasingly used by malware developers
AutoIt, a scripting language for automating Windows interface interactions, is increasingly being used by malware developers thanks to its flexibility and low learning curve, according to security researchers from Trend Micro and Bitdefender.
"Recently, we have seen an uptick in the amount of nefarious AutoIt tool code being uploaded to Pastebin," Kyle Wilhoit, a threat researcher at antivirus vendor Trend Micro, said Monday in a blog post. "One commonly seen tool, for instance, is a keylogger. Grabbing this code, anyone with bad intentions can quickly compile and run it in a matter of seconds."
"In addition to tools being found on sites like Pastebin and Pastie, we are also seeing a tremendous increase in the amount of malware utilizing AutoIt as a scripting language," Wilhoit said.
The use of AutoIt in malware development has steadily increased since 2008, Bogdan Botezatu, a senior e-threat analyst at antivirus vendor Bitdefender said Tuesday via email. The number of malware samples coded in AutoIt has recently peaked at more than 20,000 per month, he said.
"In its early days, AutoIt malware was mostly used for advertising fraud or to create self-propagation mechanisms for IM [instant messaging] worms," Botezatu said. "Nowadays, AutoIt malware ranges from ransomware to remote access applications."
One particularly sophisticated piece of AutoIt-based malware discovered recently was a version of the DarkComet RAT (remote access Trojan program), Wilhoit said. This malware opens a backdoor on the victim's machine, communicates with a remote command and control server and modifies Windows firewall policies, he said.
The DarkComet RAT has been used in targeted, APT-style, attacks in the past, including by the Syrian government to spy on political activists in the country. What's interesting about the variant found by Trend Micro is that it's written in AutoIt and has a very low antivirus detection rate.
The use of scripting languages to develop sophisticated malware is not a widespread practice, because most of these languages require an interpreter to be installed on the machine or produce very large stand-alone executable files, Botezatu said.
However, there have been exceptions. For example, the Flame cyberespionage malware used the LUA scripting language to automate some tasks without being detected by antivirus products, Botezatu said.
AutoIt is extremely intuitive and easy to use, produces compiled binaries that run out of the box on modern Windows versions and is well documented, the Bitdefender researcher said. Also, there is already a lot of malicious AutoIt code available on the Web for reuse, he said.
"Most importantly, malware created in AutoIt is extremely flexible and can be easily obfuscated, which means that a single breed of malware written in AutoIt can be repackaged and re-crafted in a number of ways to prevent detection and extend its shelf life," Botezatu said.
As scripting languages like AutoIt continue to gain popularity, more malware developers are expected to migrate toward them, Wilhoit said. "The ease of use and learning, as well as the ability to post code easily to popular dropsites make this a great opportunity for actors with nefarious intentions to propagate their tools and malware."
Source:ITworld
Amazon adds to developer choices with JavaScript SDK for Web Services
The general release of the AWS (Amazon Web Services) SDK for Node.js is available for download, allowing developers to build server-side applications in JavaScript that then can run on Amazon's cloud.
The free SDK follows a preview version that Amazon announced in December last year. One of the advantages of Node.js is that developers can scale their applications without having to deal with polling, timeouts and event loops, according to Amazon. It is based on Google's V8 JavaScript engine and includes a library of functions that work under an event-driven model.
New features added to the generally available version include bound parameters, streams, IAM (identity and access management) roles for EC2 (Elastic Compute Cloud) instances, proxies and version locking. The latter feature allows users to lock into an API version for a service, which Amazon recommends if the API is relied on for production code. This way companies can isolate themselves from changes in updates of the SDK, it said.
Applications written using the SDK can be integrated with a long list of Amazon's cloud services, including Amazon's Relational Database Service and its Virtual Private Cloud offering, which lets users create logically isolated virtual servers and an optional VPN connection to their own data center.
Recently, Amazon also announced a version of Elastic Beanstalk for Node.js-based applications. Elastic Beanstalk aims to make it easier to quickly deploy and manage applications in Amazon's cloud. The tool can also be used with Java, PHP, Python, Ruby and .Net applications.
The preferred way to install the AWS SDK for Node.js is to use the npm package manager for Node.js, according to Amazon's documentation for the kit, which also includes a configuration guide and code examples.
Source:ITworld
Google hit by building automation security FAIL
The building housing Google Australia's lavish Sydney headquarters is running the known-vulnerable Tridium Niagara building management system, and has been compromised by the Cylance researchers who have made Niagara their mission.
The researchers identified the underlying system – QNX on an embedded system – and extracted the admin password from the system's config file. After that, as the company's blog post explains, they were able to wander around the control environment pretty much at will.
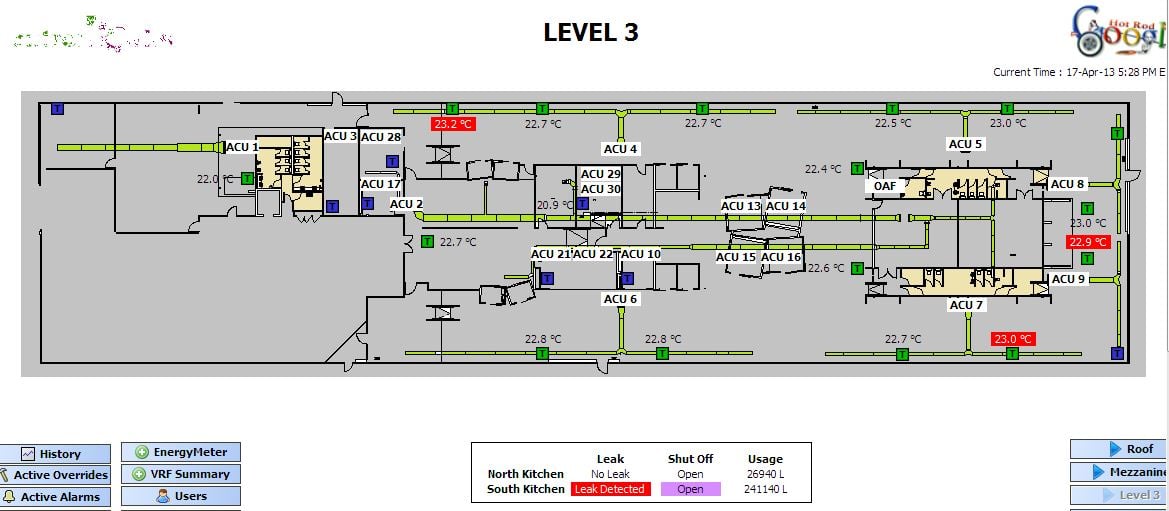
Billy Rios and Terry McCorkle demonstrate the successful attack by posting the building's Level 3 layout, water, and air-conditioning systems with the blog post. They also mention an “after hours button” they said they were “afraid to test” because of its hammer symbol in the system (hint: it probably merely activates the doors so people can get out after the doors have been switched off).
The Cylance gents admit that this vulnerability posting – which has been reported to Google – is linkbait in the service of awareness-raising.
At the time of this blog post, this exact issue affects tens of thousands of devices on the Internet and thousands of different organizations. Thank you Google for helping us raise awareness on this issue!” they write.
They noted that the Google vulnerability was present because the building in which the company resides was running an older version of the Niagara system, so there's likely to be a contractor with some explaining to do.
Source:Theregister
The researchers identified the underlying system – QNX on an embedded system – and extracted the admin password from the system's config file. After that, as the company's blog post explains, they were able to wander around the control environment pretty much at will.
Billy Rios and Terry McCorkle demonstrate the successful attack by posting the building's Level 3 layout, water, and air-conditioning systems with the blog post. They also mention an “after hours button” they said they were “afraid to test” because of its hammer symbol in the system (hint: it probably merely activates the doors so people can get out after the doors have been switched off).
The Cylance gents admit that this vulnerability posting – which has been reported to Google – is linkbait in the service of awareness-raising.
At the time of this blog post, this exact issue affects tens of thousands of devices on the Internet and thousands of different organizations. Thank you Google for helping us raise awareness on this issue!” they write.
They noted that the Google vulnerability was present because the building in which the company resides was running an older version of the Niagara system, so there's likely to be a contractor with some explaining to do.
Source:Theregister
Man Suspected of Developing and Distributing SpyEye Malware Extradited to the US
Hamza Bendelladj of Algeria, aka “Bx1,” has been extradited from Thailand – where he was arrested earlier this year while in transit from Malaysia to Egypt – to the US. He is accused of playing a critical role in developing, marketing, distributing and controlling the notorious piece of malware known as SpyEye.
The 24-year-old is charged with one count of conspiring to commit wire fraud and bank fraud, 10 counts of wire fraud, 11 counts of computer fraud, and one count of conspiracy to commit computer fraud.
If found guilty, he could spend up to 30 years in prison for conspiracy to commit wire and bank fraud, up to 5 years for conspiracy to commit computer fraud, up to 20 years for each wire fraud count, and up to 5 or 10 years for each count of computer fraud.
In addition, he could be forced to pay fines totaling $14 million (€10.6 million).
According to the US Department of Justice, between 2009 and 2011, Bendelladj and others allegedly developed, marketed and sold versions of SpyEye to other cybercriminals.
Authorities believe that Bendelladj also operated command and control (C&C) servers for the SpyEye malware.
“No violence or coercion was used to accomplish this scheme, just a computer and an Internet connection. Bendelladj’s alleged criminal reach extended across international borders, directly into victims’ homes,” said US Attorney Sally Quillian Yates.
“In a cyber-netherworld, he allegedly commercialized the wholesale theft of financial and personal information through this virus which he sold to other cybercriminals. Cybercriminals take note; we will find you. This arrest and extradition demonstrates our determination to bring you to justice.”
FBI Special Agent in Charge Mark F. Giuliano of the Atlanta Field Office commented, “The FBI has expanded its international partnerships to allow for such extraditions of criminals who know no borders.”
He added, “The federal indictment and extradition of Bendelladj should send a very clear message to those international cyber-criminals who feel safe behind their computers in foreign lands that they are, in fact, within reach.”
Source:Softpedia
Abonați-vă la:
Postări (Atom)