Se afișează postările cu eticheta Cybercrime. Afișați toate postările
Se afișează postările cu eticheta Cybercrime. Afișați toate postările
marți, 7 mai 2013
AutoIt scripting increasingly used by malware developers
AutoIt, a scripting language for automating Windows interface interactions, is increasingly being used by malware developers thanks to its flexibility and low learning curve, according to security researchers from Trend Micro and Bitdefender.
"Recently, we have seen an uptick in the amount of nefarious AutoIt tool code being uploaded to Pastebin," Kyle Wilhoit, a threat researcher at antivirus vendor Trend Micro, said Monday in a blog post. "One commonly seen tool, for instance, is a keylogger. Grabbing this code, anyone with bad intentions can quickly compile and run it in a matter of seconds."
"In addition to tools being found on sites like Pastebin and Pastie, we are also seeing a tremendous increase in the amount of malware utilizing AutoIt as a scripting language," Wilhoit said.
The use of AutoIt in malware development has steadily increased since 2008, Bogdan Botezatu, a senior e-threat analyst at antivirus vendor Bitdefender said Tuesday via email. The number of malware samples coded in AutoIt has recently peaked at more than 20,000 per month, he said.
"In its early days, AutoIt malware was mostly used for advertising fraud or to create self-propagation mechanisms for IM [instant messaging] worms," Botezatu said. "Nowadays, AutoIt malware ranges from ransomware to remote access applications."
One particularly sophisticated piece of AutoIt-based malware discovered recently was a version of the DarkComet RAT (remote access Trojan program), Wilhoit said. This malware opens a backdoor on the victim's machine, communicates with a remote command and control server and modifies Windows firewall policies, he said.
The DarkComet RAT has been used in targeted, APT-style, attacks in the past, including by the Syrian government to spy on political activists in the country. What's interesting about the variant found by Trend Micro is that it's written in AutoIt and has a very low antivirus detection rate.
The use of scripting languages to develop sophisticated malware is not a widespread practice, because most of these languages require an interpreter to be installed on the machine or produce very large stand-alone executable files, Botezatu said.
However, there have been exceptions. For example, the Flame cyberespionage malware used the LUA scripting language to automate some tasks without being detected by antivirus products, Botezatu said.
AutoIt is extremely intuitive and easy to use, produces compiled binaries that run out of the box on modern Windows versions and is well documented, the Bitdefender researcher said. Also, there is already a lot of malicious AutoIt code available on the Web for reuse, he said.
"Most importantly, malware created in AutoIt is extremely flexible and can be easily obfuscated, which means that a single breed of malware written in AutoIt can be repackaged and re-crafted in a number of ways to prevent detection and extend its shelf life," Botezatu said.
As scripting languages like AutoIt continue to gain popularity, more malware developers are expected to migrate toward them, Wilhoit said. "The ease of use and learning, as well as the ability to post code easily to popular dropsites make this a great opportunity for actors with nefarious intentions to propagate their tools and malware."
Source:ITworld
Man Suspected of Developing and Distributing SpyEye Malware Extradited to the US
Hamza Bendelladj of Algeria, aka “Bx1,” has been extradited from Thailand – where he was arrested earlier this year while in transit from Malaysia to Egypt – to the US. He is accused of playing a critical role in developing, marketing, distributing and controlling the notorious piece of malware known as SpyEye.
The 24-year-old is charged with one count of conspiring to commit wire fraud and bank fraud, 10 counts of wire fraud, 11 counts of computer fraud, and one count of conspiracy to commit computer fraud.
If found guilty, he could spend up to 30 years in prison for conspiracy to commit wire and bank fraud, up to 5 years for conspiracy to commit computer fraud, up to 20 years for each wire fraud count, and up to 5 or 10 years for each count of computer fraud.
In addition, he could be forced to pay fines totaling $14 million (€10.6 million).
According to the US Department of Justice, between 2009 and 2011, Bendelladj and others allegedly developed, marketed and sold versions of SpyEye to other cybercriminals.
Authorities believe that Bendelladj also operated command and control (C&C) servers for the SpyEye malware.
“No violence or coercion was used to accomplish this scheme, just a computer and an Internet connection. Bendelladj’s alleged criminal reach extended across international borders, directly into victims’ homes,” said US Attorney Sally Quillian Yates.
“In a cyber-netherworld, he allegedly commercialized the wholesale theft of financial and personal information through this virus which he sold to other cybercriminals. Cybercriminals take note; we will find you. This arrest and extradition demonstrates our determination to bring you to justice.”
FBI Special Agent in Charge Mark F. Giuliano of the Atlanta Field Office commented, “The FBI has expanded its international partnerships to allow for such extraditions of criminals who know no borders.”
He added, “The federal indictment and extradition of Bendelladj should send a very clear message to those international cyber-criminals who feel safe behind their computers in foreign lands that they are, in fact, within reach.”
Source:Softpedia
Syrian Electronic Army Hacks “The Onion” Twitter and Facebook Accounts
Hackers of the Syrian Electronic Army have hijacked the social media accounts of yet another news organization. Their latest victim is The Onion, the famous American news satire organization.
The hackers say they’ve hijacked a total of five Twitter accounts – TheOnion, OnionSports, ONN, TheAVClub and OnionPolitics –, and two of the publication’s Facebook accounts.
“Syrian Electronic Army Hacked today Twitter accounts and Facebook pages of The Onion satirical newspaper. And that came after that website published a news that harms the reputation of Syria and its leader,” the hackers wrote on their website.
SyriaNews has caught a glimpse of the messages published by the pro-Assad hackers from the compromised accounts.
“UN’s Ban Ki Moon condemns Syria for being struck by israel: ‘It was in the way of Jewish missiles’,” one of the tweets read.
“UN retracts report of Syrian chemical weapon use: ‘Lab tests confirm it is Jihadi body odor’,” the hackers wrote.
Shortly after recovering their accounts, representatives of The Onion have confirmed the incident, in their own manner.
“Following today’s incident in which the Syrian Electronic Army hacked into The Onion’s Twitter account, sources at America’s Finest News Source confirmed that its Twitter password has been changed to OnionMan77 in order to prevent any future cyber-attacks,” reads an article published on The Onion shortly after the breach.
The Onion has published several satirical posts related to the incident, including “The Onion’s tips on how to prevent your major media site from being hacked” and “Syrian Electronic Army has a little fun before inevitable upcoming deaths at hands of rebels.”
In addition to compromising The Onion’s social media accounts, the Syrian Electronic Army also appears to have hijacked the email accounts of at least a couple of staff members
Source:Softpedia
The hackers say they’ve hijacked a total of five Twitter accounts – TheOnion, OnionSports, ONN, TheAVClub and OnionPolitics –, and two of the publication’s Facebook accounts.
“Syrian Electronic Army Hacked today Twitter accounts and Facebook pages of The Onion satirical newspaper. And that came after that website published a news that harms the reputation of Syria and its leader,” the hackers wrote on their website.
SyriaNews has caught a glimpse of the messages published by the pro-Assad hackers from the compromised accounts.
“UN’s Ban Ki Moon condemns Syria for being struck by israel: ‘It was in the way of Jewish missiles’,” one of the tweets read.
“UN retracts report of Syrian chemical weapon use: ‘Lab tests confirm it is Jihadi body odor’,” the hackers wrote.
Shortly after recovering their accounts, representatives of The Onion have confirmed the incident, in their own manner.
“Following today’s incident in which the Syrian Electronic Army hacked into The Onion’s Twitter account, sources at America’s Finest News Source confirmed that its Twitter password has been changed to OnionMan77 in order to prevent any future cyber-attacks,” reads an article published on The Onion shortly after the breach.
The Onion has published several satirical posts related to the incident, including “The Onion’s tips on how to prevent your major media site from being hacked” and “Syrian Electronic Army has a little fun before inevitable upcoming deaths at hands of rebels.”
In addition to compromising The Onion’s social media accounts, the Syrian Electronic Army also appears to have hijacked the email accounts of at least a couple of staff members
Source:Softpedia
vineri, 3 mai 2013
Website of Iran’s Basij Force Taken Down by Cyberattacks
As the presidential elections draw near, tension mounts in Iran both in the real world and in cyberspace. On May 1, the official website of the country’s Basij military branch was taken down after a cyberattack was launched against it.
“Due to the impending vote, elements of the global arrogance have launched a new round of cyberattacks against Basij websites, particularly Basij.ir,” the force’s representatives stated according to Think Progress.
A spokesman revealed that the Basij website had faced numerous attacks over the past three years.
In the meantime, members of the Iranian hacktivist group Ashiyane Digital Security have told Softpedia they’re preparing an operation against governments and media organizations that have spread lies about Iran.
“Our mission is protect Iran from hackers & social media lies,” the group’s leader said.
“They don’t know the truth and when the government lies we will try to take them down. When Social Media lies we will try to take them down,” he added.
Source:Softpedia
Indian Politicians Hire Hackers to Spy on Their Opponents
Some Indian politicians have stopped using their smartphones for important communications after news broke out that hackers were being hired by their political opponents.
Times of India reports that hackers and security experts are being offered Rs 1 lakh ($1,852 / €1,416) and sometimes even more to breach the smartphones of ministers, members of the legislative assembly and members of parliament.
N Nityanand, CTO of Entersoft Information systems at Ameerpet, says that he has been approached on numerous occasions and offered as much money as he wanted to break into the email accounts of top politicians. Nityanand has refused for ethical reasons, but not everyone is like him.
Usually, the hackers are contacted by mediators of the political leaders who don’t name the individuals they represent. They want to be able to intercept phone calls, text messages, emails and anything else that might be of interest.
To gain control of the smartphones of politicians, the hackers send out emails that point to cleverly designed websites. When the links from the emails are clicked, a malicious software is downloaded onto the device.
Source:Softpedia
How Twitter fueled a market swoon
A fake report posted by hackers on the Associated Press Twitter feed caused the S&P 500 to drop 0.9 percent
A single tweet can be enough to cause a stock market crisis, says Christopher Matthews at TIME. We learned that last week, when hackers posted a fake report on the Associated Press Twitter feed claiming that Barack Obama had been injured in an explosion at the White House. The AP quickly flagged the tweet as fake, but not before it "sent shock waves through the market," causing the S&P 500 to drop 0.9 percent and temporarily wiping out $136 billion in stock value. The real culprit behind this latest "flash crash" isn't a hacker — it's "the proliferation of high-frequency trading." Wall Street firms use computer algorithms to make millions of trades per second, triggered by automated scans of news sources- — including Twitter — for specific words or phrases. They make money, but "when the going gets tough, these computers tend to sell quickly and run for the hills, actually reducing liquidity when the market needs it most."
Don't blow this out of proportion, say Jared Keller and Evan Applegate at Businessweek. Cases of false tweets and news reports wreaking havoc on the markets are rare. In 2011, for instance, Apple shares dipped just 1 percent (and quickly rebounded) after a false report said that Apple founder Steve Jobs had died. And when a Twitter account impersonating prominent short-seller David Einhorn tried to "induce fluctuations" in Herbalife's stock in February, the company's value underwent "no noticeable change." Still, the AP episode "highlights the potential pitfalls of relying on social networks for tradable information," especially on the heels of the Securities and Exchange Commission's announcement that companies can use social media sites, including Twitter and Facebook, "to share market-moving company announcements."
The solution is better security, says Caleb Garling in the San Francisco Chronicle. The First Amendment "prevents the government from controlling what users say on Twitter," but regulators can make social media firms beef up their protocols. False information "has the potential to be damaging to more than the financial world." Just imagine: "If the hacked AP tweet had been more believable and not as easy to discredit — say, 'U.S. Navy moving into strategic positions around North Korea' — a global emergency could have ensued." The technology sector may disdain regulation, but "other kinds of information, such as financial and health-care data, are already strictly regulated by law." It's up to the consumer to decide what to trust on Twitter, but messages shouldn't be so easy to fake.
"Other than self-restraint, which is in short supply these days, nothing much can be done to prevent any of this," says George Packer at The New Yorker. Social media sites will seek new means to "spread information, for better and worse, farther and faster than the Spanish flu." And unless regulators crack down on high-frequency traders, they "will go on using algorithms that turn milliseconds of information advantage into huge profits" — even if that information is wrong.
joi, 2 mai 2013
Java applets run wild inside Notes
Attackers with a desire to rummage around inside the PCs of Notes users can do so merely by sending HTML emails containing a Java applet or JavaScript, IBM has admitted in a security advisory.
Full Disclosure describes the effects as potentially nasty, saying "This can be used to load arbitrary Java applets from remote sources (making it an information disclosure as well as it can be used to trigger an HTTP request once the mail is previewed/opened)"
"Combined with known Java sandbox escape vulnerabilities, it can be used to fully compromise the user reading the email," the site adds.
It's not sure just what “fully compromise” means in this context, but it is not hard to imagine the consequences of a successful attack could be unpleasant, given the Notes client links to Notes apps that in turn link to databases full of a business' important information.
Sean Richmond, a senior technology consultant at Sophos, said the ability to run Java and JavaScript in an email “could be an entry to corporate assets” and also expressed mild incredulity about the vulnerabilty. “JavaScript in email attributes is considered bad.”
Things could be worse if an applet is able to emerge from Notes into a PC's Java virtual machine, a scenario Richardson hopes won't come about because email gateways' settings should be maximally hostile to .JAR files. Of course one would also imagine an email client would be maximally hostile to HTML emails calling .JAR files.
Happily, one fix is easy: just turn off the preferences that allow Java and JavaScript to run inside Notes. Another requires tickling some .ini files.
The problem affects Notes 8.5.3 and the new Notes 9. IBM promises fixes real soon now
Source:theregister
Full Disclosure describes the effects as potentially nasty, saying "This can be used to load arbitrary Java applets from remote sources (making it an information disclosure as well as it can be used to trigger an HTTP request once the mail is previewed/opened)"
"Combined with known Java sandbox escape vulnerabilities, it can be used to fully compromise the user reading the email," the site adds.
It's not sure just what “fully compromise” means in this context, but it is not hard to imagine the consequences of a successful attack could be unpleasant, given the Notes client links to Notes apps that in turn link to databases full of a business' important information.
Sean Richmond, a senior technology consultant at Sophos, said the ability to run Java and JavaScript in an email “could be an entry to corporate assets” and also expressed mild incredulity about the vulnerabilty. “JavaScript in email attributes is considered bad.”
Things could be worse if an applet is able to emerge from Notes into a PC's Java virtual machine, a scenario Richardson hopes won't come about because email gateways' settings should be maximally hostile to .JAR files. Of course one would also imagine an email client would be maximally hostile to HTML emails calling .JAR files.
Happily, one fix is easy: just turn off the preferences that allow Java and JavaScript to run inside Notes. Another requires tickling some .ini files.
The problem affects Notes 8.5.3 and the new Notes 9. IBM promises fixes real soon now
Source:theregister
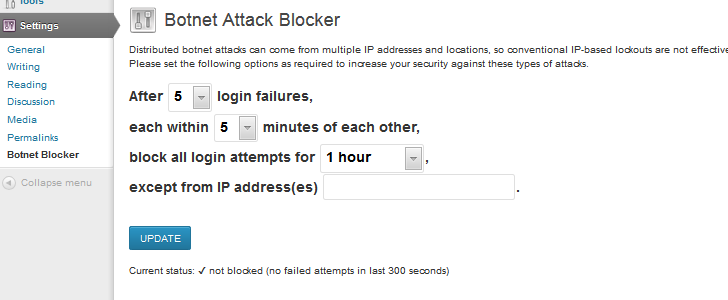
Botnet Attack Blocker for WordPress Protects Sites Against Brute-Force Attacks
An interesting WordPress plugin released a few days ago could be of great aid to website administrators that want to make sure their sites are protected against the recent brute-force attacks.
Many websites are configured to block out an IP address after too many failed login attempts.
However, the brute-force attacks analyzed by experts rely on a botnet to crack passwords. Since each attempt to break the password can come from a different IP address, 1,000 computers are capable of trying out 5,000 combinations if the failed login attempts limit is set to 5.
This is where the Botnet Attack Blocker steps in. According to its author, the plugin ignores the different IP addresses and blocks attackers even if they use a large number of bots.
For instance, if 5 failed login attempts are set, 1,000 computers will only be allowed to try out 5 passwords, regardless of the fact that they have different IPs.
Users of Botnet Attack Blocker can select the number of allowed login attempts, the time interval between failures, and for how long to block logins. Admins can whitelist their own IP address to make sure they can access the website even during an attack.
Source:Softpedia
Many websites are configured to block out an IP address after too many failed login attempts.
However, the brute-force attacks analyzed by experts rely on a botnet to crack passwords. Since each attempt to break the password can come from a different IP address, 1,000 computers are capable of trying out 5,000 combinations if the failed login attempts limit is set to 5.
This is where the Botnet Attack Blocker steps in. According to its author, the plugin ignores the different IP addresses and blocks attackers even if they use a large number of bots.
For instance, if 5 failed login attempts are set, 1,000 computers will only be allowed to try out 5 passwords, regardless of the fact that they have different IPs.
Users of Botnet Attack Blocker can select the number of allowed login attempts, the time interval between failures, and for how long to block logins. Admins can whitelist their own IP address to make sure they can access the website even during an attack.
Source:Softpedia
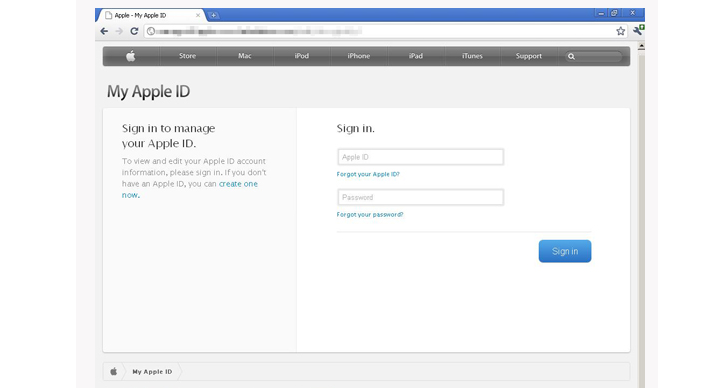
Apple ID Phishing Scams on the Rise, Trend Micro Experts Find
Phishing scams that target the Apple IDs of users are not uncommon, but experts from security firm Trend Micro say they’ve identified a spike in the number of websites designed to trick users into handing over their information.
After analyzing the URLs of the Apple ID phishing pages, experts noticed that they were all hosted in a folder called “~flight.” A total of 110 websites have been found hosted on a single IP address registered to an ISP in the Houston area.
The phishing sites are well designed and they target not only US users, but also people from France and the UK.
In addition, some of the scams are designed to steal more than just Apple IDs. They request victims to enter even their billing address and credit card information.
Cybercriminals lure victims to these phishing sites with bogus Apple emails which inform recipients that their accounts will expire unless they provide some information.
Experts advise users always to make sure that the site they enter their information on is secure. The URL should start with “https” and the browser should display a padlock icon in the address bar.
Source:Softpedia
Chinese Hackers Steal Info from US Defense Contractor for Several Years [Bloomberg]
Starting with 2007, at least 30 US defense contractors have been targeted by the Comment Crew, the notorious hacker collective that’s believed to be funded by the Chinese government. One of these companies was QinetiQ North America.
QinetiQ provides the US government with software used by the military, drones, robots, helicopters, satellites, weapon systems, and many other technologies that contribute to national security.
According to an extensive report from Bloomberg, the hackers targeted the company since at least 2007. Since at least 2009, it’s believed they’d been continuously operating in the organization’s networks, stealing a wide range of classified documents.
In one of the attacks, that took place in 2009, the hackers raided at least 151 machines of the firm’s Technology Solutions Group (TSG) over a 251-day period, stealing 20 gigabytes of data before being blocked.
1.3 million pages of documents, including ones containing highly sensitive military information, were stolen at the time.
In the first two and half years, it’s believed the Comment Crew – whose activities have been detailed in a recent report published by security firm Mandiant – stole over 13,000 internal passwords.
In 2010, HBGary, the security firm hacked in 2011 by Anonymous, was hired by QinetiQ along with Terremark to investigate the attacks. HBGary almost immediately identified malicious software on most of QinetiQ’s computers.
The security companies managed to clean up QinetiQ’s systems, but this only lasted for a couple of months, after which the FBI notified the contractor about another data breach.
Some say China might have already put to good use the information stolen from the firm. In April 2012, the Chinese military unveiled a bomb disposal robot that was very similar to QinetiQ’s Dragon Runner.
The technology for the Chinese robot might have been obtained from the computer of a specialist that focused on the embedded software on microchips that controlled military robots. His computer was among those infected.
Interestingly, in May 2012, QinetiQ was awarded a $4.7 million (€3.6 million) cybersecurity contract from the US Transportation Department.
Source:Bloomberg
QinetiQ provides the US government with software used by the military, drones, robots, helicopters, satellites, weapon systems, and many other technologies that contribute to national security.
According to an extensive report from Bloomberg, the hackers targeted the company since at least 2007. Since at least 2009, it’s believed they’d been continuously operating in the organization’s networks, stealing a wide range of classified documents.
In one of the attacks, that took place in 2009, the hackers raided at least 151 machines of the firm’s Technology Solutions Group (TSG) over a 251-day period, stealing 20 gigabytes of data before being blocked.
1.3 million pages of documents, including ones containing highly sensitive military information, were stolen at the time.
In the first two and half years, it’s believed the Comment Crew – whose activities have been detailed in a recent report published by security firm Mandiant – stole over 13,000 internal passwords.
In 2010, HBGary, the security firm hacked in 2011 by Anonymous, was hired by QinetiQ along with Terremark to investigate the attacks. HBGary almost immediately identified malicious software on most of QinetiQ’s computers.
The security companies managed to clean up QinetiQ’s systems, but this only lasted for a couple of months, after which the FBI notified the contractor about another data breach.
Some say China might have already put to good use the information stolen from the firm. In April 2012, the Chinese military unveiled a bomb disposal robot that was very similar to QinetiQ’s Dragon Runner.
The technology for the Chinese robot might have been obtained from the computer of a specialist that focused on the embedded software on microchips that controlled military robots. His computer was among those infected.
Interestingly, in May 2012, QinetiQ was awarded a $4.7 million (€3.6 million) cybersecurity contract from the US Transportation Department.
Source:Bloomberg
Ticket Resellers Launch DDOS Attacks Against Primary Agents to Keep Prices High
Distributed denial-of-service (DDOS) attacks are not used only by hacktivists to make a point or by cybercriminals to cover up fraud. They’re also utilized by companies for business logic attacks.
One example of such a business logic DDOS attack is revealed by Vice President and Distinguished Analyst in Gartner Research Avivah Litan.
Litan says ticket resellers in the secondary market are launching DDOS attacks against primary online ticket sellers – the companies that host the event or ones that sell tickets on their behalf at retail prices. This strategy allows resellers to keep ticket prices high.
“Ticket resellers in the secondary market want to keep the inventory on the event’s available seats low so they can keep their prices high,” the expert explained.
Source:softpedia.com
Cyber crooks dupe victims with bogus Microsoft security alerts
Webroot has detected a new wave of bogus Microsoft-themed cyber scams, looking to dupe web users with bogus security notifications.
The security firm reported detecting a number of scams targeting users with malware-laden messages masquerading as alerts from Microsoft in a blog post on Tuesday.
"Recently we have seen an increase in fake Microsoft scams, which function by tricking people into thinking that their PC is infected," wrote Webroot's Roy Tobin. He added that the cyber crooks use a variety of techniques to get the messages in front of their victims.
"There are a number of ways to figure out that this is a false alert. The first is that it's a website message and not a program; the second is that location of the website will be a random string of letters," he said.
"These websites will normally only stay active for 24-48 hours before they are pulled down. The websites' primary function is to get you to run a ‘removal tool' called ‘security cleaner'. This file is the infection and, if ran, will infect the PC and start displaying pop-ups."
The Webroot researcher said that the scams are not terribly advanced, and as long as users don't click on the malicious messages they will stay safe.
"At this stage [when the message appears], the PC is not infected so it's safe to close the browser and ignore any alerts from the website. Noting the website that displayed the message is good idea as you can notify the webmaster (if it's a legitimate website)," wrote Tobin.
Microsoft is one of many big brands used by cyber criminals to make the phishing messages look more legitimate. Last month, McAfee detected a cyber scam that used Facebook and LinkedIn to spread malware.
Source:V3
U.S. Department of Labor website hacked and redirecting to malicious code
During the last few hours we have identified that one the U.S. Department of Labor website has been hacked and it is serving malicious code.
Clarification:
The website affected is the The Department of Labor (DOL) Site Exposure Matrices (SEM) Website
“The Department of Labor (DOL) Site Exposure Matrices (SEM) Website is a repository of information gathered from a variety of sources regarding toxic substances present at Department of Energy (DOE) and Radiation Exposure Compensation Act (RECA) facilities covered under Part E of the Energy Employees Occupational Illness Compensation Program Act (EEOICPA)”
As you can see in the following UrlQuery report the website is including code from the malicious server dol[.]ns01[.]us:
Once you visit the website the following file is included:
www[.]sem[.]dol[.]gov/scripts/textsize.js that contains the following code:
Source:alienvault
Clarification:
The website affected is the The Department of Labor (DOL) Site Exposure Matrices (SEM) Website
“The Department of Labor (DOL) Site Exposure Matrices (SEM) Website is a repository of information gathered from a variety of sources regarding toxic substances present at Department of Energy (DOE) and Radiation Exposure Compensation Act (RECA) facilities covered under Part E of the Energy Employees Occupational Illness Compensation Program Act (EEOICPA)”
As you can see in the following UrlQuery report the website is including code from the malicious server dol[.]ns01[.]us:
Once you visit the website the following file is included:
www[.]sem[.]dol[.]gov/scripts/textsize.js that contains the following code:
Source:alienvault
Critics condemn proposed internet wiretapping bill
Government officials are reportedly prepping legislation that will require web companies to put FBI used backdoor wiretapping capabilities into their websites.
According to The Washington Post, the legislation would affect companies like Google and Facebook. FBI officials say the proposed legislation would allow them to tap into web communications of supposed terrorists.
However, web advocacy groups fear the backdoor implementation could cause risk to security and stifle innovation.
"Implementing such access would be cumbersome when not impossible, and the system would instantly become a target for cyber security intrusions," said Computer & Communications Industry Association president and chief executive officer Ed Black.
"All of these impacts would fall disproportionately on small businesses that don't have the resources of the larger companies."
The proposed legislation would require major web-based companies to offer law enforcement backdoor capabilities to implement wiretaps. If companies do not build out the tool they stand to be fined as part of the legislation.
Proposed legislation would come as an amendment to the Communications Assistance for Law Enforcement Act (CALEA). The bill was introduced in 1994 to clearly state what a private telecommunications firm's responsibilities are when dealing with law enforcement agencies.
Bill opponents say the legislation would be ineffective if approved. According to Center for Democracy & Technology senior staff technologist Joe Hall, the bill doesn't fix the problem as bad actors would be able to hide their identity online.
"The sad irony is that this is likely to be ineffective. Building a communications tool today is a homework project for undergraduates," said Hall.
"So much is based on open source and can be readily customized. Criminals and other bad actors will simply use homemade communication services based offshore, making them even harder to monitor."
US authorities have continued to look for ways to better access online information for criminal cases. Along with the proposed wiretapping laws, the Senate is expected to vote on a revised CISPA bill later this year.
Gaming app ENSLAVES punter PCs in Bitcoin mining ring
A competitive gaming company has admitted that for two weeks in April its software client was hijacking league members' PCs to mine Bitcoins.
In an eyebrow-raising turn of events, the company, ESEA Gaming, admitted on Wednesday that its software client had been running Bitcoin-mining algorithms on customer PCs since April 14, generating over $3,700 worth of the virtual currency – not to mention a likely uptick in the electricity bills of the unwitting punters whose graphics cards' GPUs been forced to mine the virtual currency.
ESEA is a competitive gaming company that lets paying punters play various video games competitively, with the chance of a cash prize as they rise through the ranks. It uses a bespoke software client to prevent cheating, and it was this software client that was loaded with Bitcoin mining routines.
The Bitcoin mining software had been originally rolled out in a test on ESEA Gaming admin accounts, the company's co-founder Eric Thunberg explained in a forum post using the handle lpkane. But the test didn't generate many Bitcoins (two in two days) and was shut down – or so Thunberg thought.
In fact, the miner wasn't shut down. Rather, it was rolled out across ESEA's entire user base.
An ESEA employee who was involved in the tests "has been using the test code for his own personal gain since April 13, 2013," the company wrote in an official statement on Monday. "We are extremely disappointed and concerned by the unauthorized actions of this unauthorized individual. As of this morning, ESEA has made sure that all Bitcoin mining has stopped. ESEA is also in the process of taking all necessary steps internally to ensure that nothing like this ever happens again."
The program used player GPUs to perform the complex mathematical operations required to mine Bitcoins, and generated 29.27627734 Bitcoins for the ESEA employee.
ESEA became aware of the Bitcoin mining after concerned users made posts to the forum complaining of high GPU utilization, even when idle.
The unauthorized two-week long spell of mining apparently took Thunberg by surprise, who wrote in a later post to the forum:
as of the client update released in the last hour, all the btc stuff is out which should solve the gpu and av warnings, and in a blatant attempt to buy back your love (and less likely your trust), i'm going to do the following:
1. 100% of the funds are going into the s14 prize pot, so at the very least your melted gpus contributed to a good cause
2. every user who was premium this month will get a free one month premium code which they can use whenever and for whomever they like, and you'll find the code under manage accounts -> premium codes
Along with the prize pot, ESEA gaming is also donating double the value of the mined Bitcoins – $7,427.10 at current market rates – to the American Cancer Society.
"While it's incredibly disturbing and disappointing that this happened, we’re committed to improving ourselves and rebuilding trust with our community," the company wrote.
The case serves to highlight how the virtual currency's recent dramatic rise in valuation relative to the US dollar has attracted speculators, chancers, and criminals in droves. The ESEA case follows the re-emergence of Bitcoin-mining malware earlier in April, along with a variety of other money-grubbing squint-and-they're-legal schemes.
"If we had found out on our own that the miner was running we would have killed it anyway because a) we'd already decided it wasn't worth it, and b) there are far less shady ways to make money," Thunberg wrote in reply to a forum user
Source:theregister
Hackers open malware backdoor in Apache webservers
A new threat is targeting Apache webservers, which are among the most widely-used webservers in the world, according to researchers at security firms ESET and Sucuri.
The threat is a highly advanced and stealthy backdoor being used to drive traffic to malicious websites carrying Blackhole exploit packs.
Researchers have named the backdoor Linux/Cdorked.A, and have described it as the most sophisticated Apache backdoor to date.
“The Linux/Cdorked.A backdoor does not leave traces on the hard-disk other than a modified httpd file, the daemon (or service) used by Apache,” said Pierre-Marc Bureau, ESET security intelligence program manager.
“All information related to the backdoor is stored in shared memory on the server, making detection difficult and hampering analysis."
In addition, Linux/Cdorked.A takes other steps to avoid detection, both on the compromised webserver and web browsers of computers visiting it.
“The backdoor’s configuration is sent by the attacker using HTTP requests that are not only obfuscated, but also not logged by Apache, reducing the likelihood of detection by conventional monitoring tools,” said Righard Zwienenberg, ESET senior researcher.
“The configuration is stored in memory, meaning no command and control information for the backdoor is visible, making forensic analysis complex,” he said.
The Blackhole exploit kit is a popular and prevalent exploit kit using zero-day and known exploits, to take control of systems when users visit a site that is comprised and infected by the Blackhole kit.
When someone visits a compromised webserver, they are not simply redirected to a malicious website and a web cookie is set in the browser so the backdoor will not send them there a second time.
The web cookie is not set on the administrator pages. The backdoor checks the visitor’s referrer field and if they are redirected to the webpage from a URL that has certain key words in it, like "admin" or "cpanel", no malicious content is served.
ESET has called on system administrators to check their servers and verify that they are not affected by this threat.
A free detection tool, detailed instructions on how to check for the backdoor and a full technical analysis of Linux/Cdorked.A are available on ESET’s WeLiveSecurity.com site in the Linux/Cdorked blog post.
Source:ComputerWeekley
The threat is a highly advanced and stealthy backdoor being used to drive traffic to malicious websites carrying Blackhole exploit packs.
Researchers have named the backdoor Linux/Cdorked.A, and have described it as the most sophisticated Apache backdoor to date.
“The Linux/Cdorked.A backdoor does not leave traces on the hard-disk other than a modified httpd file, the daemon (or service) used by Apache,” said Pierre-Marc Bureau, ESET security intelligence program manager.
“All information related to the backdoor is stored in shared memory on the server, making detection difficult and hampering analysis."
In addition, Linux/Cdorked.A takes other steps to avoid detection, both on the compromised webserver and web browsers of computers visiting it.
“The backdoor’s configuration is sent by the attacker using HTTP requests that are not only obfuscated, but also not logged by Apache, reducing the likelihood of detection by conventional monitoring tools,” said Righard Zwienenberg, ESET senior researcher.
“The configuration is stored in memory, meaning no command and control information for the backdoor is visible, making forensic analysis complex,” he said.
The Blackhole exploit kit is a popular and prevalent exploit kit using zero-day and known exploits, to take control of systems when users visit a site that is comprised and infected by the Blackhole kit.
When someone visits a compromised webserver, they are not simply redirected to a malicious website and a web cookie is set in the browser so the backdoor will not send them there a second time.
The web cookie is not set on the administrator pages. The backdoor checks the visitor’s referrer field and if they are redirected to the webpage from a URL that has certain key words in it, like "admin" or "cpanel", no malicious content is served.
ESET has called on system administrators to check their servers and verify that they are not affected by this threat.
A free detection tool, detailed instructions on how to check for the backdoor and a full technical analysis of Linux/Cdorked.A are available on ESET’s WeLiveSecurity.com site in the Linux/Cdorked blog post.
Source:ComputerWeekley
‘Content spoofing’ a major website vulnerability, study finds
A close look at vulnerabilities in about 15,000 websites found 86% had at least one serious hole that hackers could exploit, and content spoofing was the most prevalent vulnerability, identified in over half of the sites, according to WhiteHat Securitys annual study published today.
Content spoofing is a way to get a website to display content from the attacker, says Jeremiah Grossman, CTO at WhiteHat, an IT security vendor. A criminal might do this to steal sensitive customer information or simply to embarrass the owners of a website. In any event, in content spoofing the fake content is not actually on the website as it would be in a web defacement, but simply appears to be there, Grossman points out.
The Open Web Application Security Project (OWASP) group says content spoofing is also sometimes referred to as content injection or virtual defacement, and its an attack made possible by an injection vulnerability in a web application that does not properly handle user-supplied data.
[SECURITY SCOOP: Phishing tactics and how hackers get away with it]
The content spoofing attack can supply content to a web application that is reflected back to the user, whos presented with a modified page under the context of the trusted domain, according to OWASP. Its said to be similar to a cross-site scripting attack but uses other techniques to modify the page for malicious reasons.
The annual WhiteHat Website Security Statistics Report examined vulnerabilities found over the course of 2012 in the 15,000 websites of 650 companies and government agencies for which it provides web application vulnerability assessments. These range from financial, manufacturing, technology, entertainment, energy to media, and government.
The top 15 vulnerability classes for websites are said to be cross-site scripting; information leakage; content spoofing; cross-site request forgery; brute force; insufficient transport layer protection; insufficient authorization; SQL injection; session fixation; fingerprinting; URL redirector abuse; directory indexing; abuse of functionality; predictable resource location; and HTTP response splitting.Grossman says there were a few unexpected findings related to how quickly organizations fixed vulnerabilities when taking into account how much theyd invested in application security training for their programmers.
Emphasis on training was correlated with 40% fewer website vulnerabilities and a 59% faster rate of resolving them than in organizations that didnt do training. But the actual remediation rate to close all the holes related to the vulnerabilities was 12% less than in organizations without training. Grossman says WhiteHats analysis indicates that the poorest rates of remediation overall are associated with organizations where their regulatory compliance requirements are the No.1 driver for resolving vulnerabilities. If the vulnerability wasnt tied to compliance, it was ignored.
When organizations website vulnerabilities go unresolved, compliance was cited as the #1 reason, closely followed by risk reduction, according to the WhiteHat study. The study also found the best remediation rates occurred when customers or partners demanded it.
Other findings in the website 2012 vulnerability study show:
85% of organizations use some variety of application security testing in pre-production website environments
55% have a Web Application Firewall in some state of deployment
In the event of of a website data or system breach, 79% said the Security Department would be accountable.
23% experienced a data or system breach as a result of an application-layer vulnerability.
Source:Network World
Content spoofing is a way to get a website to display content from the attacker, says Jeremiah Grossman, CTO at WhiteHat, an IT security vendor. A criminal might do this to steal sensitive customer information or simply to embarrass the owners of a website. In any event, in content spoofing the fake content is not actually on the website as it would be in a web defacement, but simply appears to be there, Grossman points out.
The Open Web Application Security Project (OWASP) group says content spoofing is also sometimes referred to as content injection or virtual defacement, and its an attack made possible by an injection vulnerability in a web application that does not properly handle user-supplied data.
[SECURITY SCOOP: Phishing tactics and how hackers get away with it]
The content spoofing attack can supply content to a web application that is reflected back to the user, whos presented with a modified page under the context of the trusted domain, according to OWASP. Its said to be similar to a cross-site scripting attack but uses other techniques to modify the page for malicious reasons.
The annual WhiteHat Website Security Statistics Report examined vulnerabilities found over the course of 2012 in the 15,000 websites of 650 companies and government agencies for which it provides web application vulnerability assessments. These range from financial, manufacturing, technology, entertainment, energy to media, and government.
The top 15 vulnerability classes for websites are said to be cross-site scripting; information leakage; content spoofing; cross-site request forgery; brute force; insufficient transport layer protection; insufficient authorization; SQL injection; session fixation; fingerprinting; URL redirector abuse; directory indexing; abuse of functionality; predictable resource location; and HTTP response splitting.Grossman says there were a few unexpected findings related to how quickly organizations fixed vulnerabilities when taking into account how much theyd invested in application security training for their programmers.
Emphasis on training was correlated with 40% fewer website vulnerabilities and a 59% faster rate of resolving them than in organizations that didnt do training. But the actual remediation rate to close all the holes related to the vulnerabilities was 12% less than in organizations without training. Grossman says WhiteHats analysis indicates that the poorest rates of remediation overall are associated with organizations where their regulatory compliance requirements are the No.1 driver for resolving vulnerabilities. If the vulnerability wasnt tied to compliance, it was ignored.
When organizations website vulnerabilities go unresolved, compliance was cited as the #1 reason, closely followed by risk reduction, according to the WhiteHat study. The study also found the best remediation rates occurred when customers or partners demanded it.
Other findings in the website 2012 vulnerability study show:
85% of organizations use some variety of application security testing in pre-production website environments
55% have a Web Application Firewall in some state of deployment
In the event of of a website data or system breach, 79% said the Security Department would be accountable.
23% experienced a data or system breach as a result of an application-layer vulnerability.
Source:Network World
Despite hack, security experts urge no fear of Google Glass
The security risk Google Glass poses to companies is no greater than smartphones or other technology that someone could use to secretly record video and snap pictures, experts say.
Google Glass and its potential security risks came under scrutiny with the recent jailbreaking of the headset that many see as the start of wearable computing as a mass market.
The model rooted by Android and iOS developer Jay Freeman was sold only to developers. Glass is not yet available to the general public.
Freeman cracked Glass in two hours by exploiting a well-known vulnerability in Android 4.0.4, the version of the operating system that ships with the device. Once in, Freeman was able to fully control the device, bypassing the security mechanisms put in place by Google. In general, tech-savvy people will jailbreak a device in order to run applications or to modify it in ways not allowed by the manufacturer.
The Glass break-in did not surprise Tim Bray, developer advocate for Google. "Yes, Glass is hackable. Duh," he said on Twitter.
In an interview with Forbes, Freeman was not yet sure what he could do with the device now that he had access to its software. However, Jason Perlow, senior technology editor for ZDNet, opined that Glass could be modified to secretly record video and take pictures without the user knowing.
As a recording device, the current version of Glass has serious limitations. With roughly 12GB of usable storage, there is not much room for a lot of video, although that is plenty of capacity for pictures.
Battery life is also not great. A person reading email and taking some pictures and short video could get roughly five hours, according to a review on Engadget. The maximum time would fall dramatically if someone took a lot of video.
These limitations would make Glass a weak alternative to small video devices already available if someone wanted to secretly record in an office, Anton Chuvakin, analyst for Gartner said Wednesday.
"It's completely unrealistic, but exciting to talk about," Chuvakin said of using Google Glass in a clandestine operation.
Because of the hardware limitations, jailbreaking the device also did not add much more risk. "To me, the risk of a rooted Glass device is similar to a rooted smartphone," Chuvakin said.
In addition to Glass' weak capabilities as a recorder, it is also far more expensive than much better stealthy video equipment. "Glass could certainly be used for espionage, but it is a very expensive toy to use for that purpose and has little to no advantage over already existing methods," said Chester Wisniewski, a senior security adviser for Sophos.
The bigger security issue with the current version of Glass is not having a mechanism to set a password in order to use the device, Wisniewski said. "But we can assume that a production ready version would not ship with such shoddy security."
Source:CSO
D-Link publishes beta patches for IP camera flaws
D-Link has published beta patches for vulnerabilities in the firmware of many of its IP surveillance cameras, which could allow a hacker to intercept a video stream.
The company said on its support forum that it will publish a full release of the upgraded firmware within a month. Some of D-Link's consumer IP cameras in its Cloud product line will automatically receive the updates.
"We are releasing beta firmware with the security patch for customers who want to manually update their cameras immediately," a D-Link administrator wrote on the company's support forum.
The administrator also posted instructions for how to upgrade the firmware. Users should not upgrade over a wireless connection, as an error could break the camera.
Identical notices were published on the pages for other affected products. The updates come after Core Security published on Monday details of five vulnerabilities in D-Link's firmware, which is used in more than a dozen of its products.
D-Link's IP video cameras can take stills and record video and can be managed through web-based control panels or mobile devices. Core found a range of problems, including hard-coded credentials and authentication issues that could allow an attacker access via the RTSP (real time streaming protocol).
The technical details were posted in the Full Disclosure section of Seclists.org. Some of the products have been phased out by D-Link, according to the company's website.
Source:ComputerWorld
Abonați-vă la:
Postări (Atom)