The U.S. government has demanded that major Internet companies divulge users' stored passwords, according to two industry sources familiar with these orders, which represent an escalation in surveillance techniques that has not previously been disclosed.
If the government is able to determine a person's password, which is typically stored in encrypted form, the credential could be used to log in to an account to peruse confidential correspondence or even impersonate the user. Obtaining it also would aid in deciphering encrypted devices in situations where passwords are reused.
"I've certainly seen them ask for passwords," said one Internet industry source who spoke on condition of anonymity. "We push back."
A second person who has worked at a large Silicon Valley company confirmed that it received legal requests from the federal government for stored passwords. Companies "really heavily scrutinize" these requests, the person said. "There's a lot of 'over my dead body.'"
Some of the government orders demand not only a user's password but also the encryption algorithm and the so-called salt, according to a person familiar with the requests. A salt is a random string of letters or numbers used to make it more difficult to reverse the encryption process and determine the original password. Other orders demand the secret question codes often associated with user accounts.
A Microsoft spokesperson would not say whether the company has received such requests from the government. But when asked whether Microsoft would divulge passwords, salts, or algorithms, the spokesperson replied: "No, we don't, and we can't see a circumstance in which we would provide it."
Google also declined to disclose whether it had received requests for those types of data. But a spokesperson said the company has "never" turned over a user's encrypted password, and that it has a legal team that frequently pushes back against requests that are fishing expeditions or are otherwise problematic. "We take the privacy and security of our users very seriously," the spokesperson said.
A Yahoo spokeswoman would not say whether the company had received such requests. The spokeswoman said: "If we receive a request from law enforcement for a user's password, we deny such requests on the grounds that they would allow overly broad access to our users' private information. If we are required to provide information, we do so only in the strictest interpretation of what is required by law."
Apple, Facebook, AOL, Verizon, AT&T, Time Warner Cable, and Comcast did not respond to queries about whether they have received requests for users' passwords and how they would respond to them.
Richard Lovejoy, a director of the Opera Software subsidiary that operates FastMail, said he doesn't recall receiving any such requests but that the company still has a relatively small number of users compared with its larger rivals. Because of that, he said, "we don't get a high volume" of U.S. government demands.
The FBI declined to comment.
Some details remain unclear, including when the requests began and whether the government demands are always targeted at individuals or seek entire password database dumps. The Patriot Act has been used to demand entire database dumps of phone call logs, and critics have suggested its use is broader. "The authority of the government is essentially limitless" under that law, Sen. Ron Wyden, an Oregon Democrat who serves on the Senate Intelligence committee, said at a Washington event this week.
Large Internet companies have resisted the government's requests by arguing that "you don't have the right to operate the account as a person," according to a person familiar with the issue. "I don't know what happens when the government goes to smaller providers and demands user passwords," the person said.
An attorney who represents Internet companies said he has not fielded government password requests, but "we've certainly had reset requests -- if you have the device in your possession, than a password reset is the easier way."
Cracking the codes
Even if the National Security Agency or the FBI successfully obtains an encrypted password, salt, and details about the algorithm used, unearthing a user's original password is hardly guaranteed. The odds of success depend in large part on two factors: the type of algorithm and the complexity of the password.
Algorithms, known as hash functions, that are viewed as suitable for scrambling stored passwords are designed to be difficult to reverse. One popular hash function called MD5, for instance, transforms the phrase "National Security Agency" into this string of seemingly random characters: 84bd1c27b26f7be85b2742817bb8d43b. Computer scientists believe that, if a hash function is well-designed, the original phrase cannot be derived from the output.
But modern computers, especially ones equipped with high-performance video cards, can test passwords scrambled with MD5 and other well-known hash algorithms at the rate of billions a second. One system using 25 Radeon-powered GPUs that was demonstrated at a conference last December tested 348 billion hashes per second, meaning it would crack a 14-character Windows XP password in six minutes.
The best practice among Silicon Valley companies is to adopt far slower hash algorithms -- designed to take a large fraction of a second to scramble a password -- that have been intentionally crafted to make it more difficult and expensive for the NSA and other attackers to test every possible combination.
One popular algorithm, used by Twitter and LinkedIn, is called bcrypt. A 2009 paper (PDF) by computer scientist Colin Percival estimated that it would cost a mere $4 to crack, in an average of one year, an 8-character bcrypt password composed only of letters. To do it in an average of one day, the hardware cost would jump to approximately $1,500.
But if a password of the same length included numbers, asterisks, punctuation marks, and other special characters, the cost-per-year leaps to $130,000. Increasing the length to any 10 characters, Percival estimated in 2009, brings the estimated cracking cost to a staggering $1.2 billion.
As computers have become more powerful, the cost of cracking bcrypt passwords has decreased. "I'd say as a rough ballpark, the current cost would be around 1/20th of the numbers I have in my paper," said Percival, who founded a company called Tarsnap Backup, which offers "online backups for the truly paranoid." Percival added that a government agency would likely use ASICs -- application-specific integrated circuits -- for password cracking because it's "the most cost-efficient -- at large scale -- approach."
While developing Tarsnap, Percival devised an algorithm called scrypt, which he estimates can make the "cost of a hardware brute-force attack" against a hashed password as much as 4,000 times greater than bcrypt.
Bcrypt was introduced (PDF) at a 1999 Usenix conference by Niels Provos, currently a distinguished engineer in Google's infrastructure group, and David Mazières, an associate professor of computer science at Stanford University.
With the computers available today, "bcrypt won't pipeline very well in hardware," Mazières said, so it would "still be very expensive to do widespread cracking."
Even if "the NSA is asking for access to hashed bcrypt passwords," Mazières said, "that doesn't necessarily mean they are cracking them." Easier approaches, he said, include an order to extract them from the server or network when the user logs in -- which has been done before -- or installing a keylogger at the client.
Source:Cnet
duminică, 28 iulie 2013
Fortune 500 companies give social media a thumbs-up
It appears the world's biggest moneymakers are paying increasing attention to social media.
A new report by the University of Massachusetts Dartmouth takes a look at how often companies on Fortune Magazine's Fortune 500 list are using social-media sites like Facebook, Twitter, Google+, Instagram, YouTube, Foursquare, and Pinterest. And the answer is: a lot.
Of those Fortune 500 companies, 77 percent keep active Twitter accounts, 70 percent have a Facebook page, and 69 percent have YouTube accounts. All these stats are up over last year -- with 4 percent more companies keeping Twitter accounts, 4 percent more having a Facebook page, and 7 percent more on YouTube.
Other social networks aren't as popular with the Fortune 500 companies, but they still have some presence. According to the report, 35 percent of companies have an active Google+ account. Of the 500 companies, 44 are on Instagram, 44 are on Foursquare, and 45 have Pinterest accounts.
"Due to the hugely influential role that these companies play in the business world, studying their adoption and use of social-media tools offers important insights into the future of commerce," the report reads. "These corporations provide a look at emergent social-media trends among America's most successful companies."
Not surprisingly, the company that tops the list in social-media activity is a social network itself -- Facebook. Ranked 482 on the Fortune 500 list, Facebook has more than 8.5 million Twitter followers and more than 92 million Facebook fans.
Other leading companies on Twitter include Google, Starbucks, and Whole Foods. While popular Facebook companies included Coca-Cola, Walt Disney, and Starbucks. (See graphs below.)
In addition to being more active on social media, Fortune 500 companies are also blogging more. This year, at 34 percent, more companies than ever have a public facing blog. Currently, 171 companies blog, including two of the top five Fortune 500 companies: Walmart and Exxon.
"This is a group that now seems comfortable and even excited with its newfound ability to engage its vendors, partners, customers, and others in ways that could not have been imagined when most of their corporations began," the report reads. "Judging by the increased use of tools, fans, and followers, they are making some very powerful new connections."
Source:Cnet
A new report by the University of Massachusetts Dartmouth takes a look at how often companies on Fortune Magazine's Fortune 500 list are using social-media sites like Facebook, Twitter, Google+, Instagram, YouTube, Foursquare, and Pinterest. And the answer is: a lot.
Of those Fortune 500 companies, 77 percent keep active Twitter accounts, 70 percent have a Facebook page, and 69 percent have YouTube accounts. All these stats are up over last year -- with 4 percent more companies keeping Twitter accounts, 4 percent more having a Facebook page, and 7 percent more on YouTube.
Other social networks aren't as popular with the Fortune 500 companies, but they still have some presence. According to the report, 35 percent of companies have an active Google+ account. Of the 500 companies, 44 are on Instagram, 44 are on Foursquare, and 45 have Pinterest accounts.
"Due to the hugely influential role that these companies play in the business world, studying their adoption and use of social-media tools offers important insights into the future of commerce," the report reads. "These corporations provide a look at emergent social-media trends among America's most successful companies."
Not surprisingly, the company that tops the list in social-media activity is a social network itself -- Facebook. Ranked 482 on the Fortune 500 list, Facebook has more than 8.5 million Twitter followers and more than 92 million Facebook fans.
Other leading companies on Twitter include Google, Starbucks, and Whole Foods. While popular Facebook companies included Coca-Cola, Walt Disney, and Starbucks. (See graphs below.)
In addition to being more active on social media, Fortune 500 companies are also blogging more. This year, at 34 percent, more companies than ever have a public facing blog. Currently, 171 companies blog, including two of the top five Fortune 500 companies: Walmart and Exxon.
"This is a group that now seems comfortable and even excited with its newfound ability to engage its vendors, partners, customers, and others in ways that could not have been imagined when most of their corporations began," the report reads. "Judging by the increased use of tools, fans, and followers, they are making some very powerful new connections."
Source:Cnet
Google doodle honors birthday of biophysicist Rosalind Franklin
Google devoted its doodle on Thursday to mark the 93rd birthday of Rosalind Franklin, a British biophysicist and X-ray crystallographer who made great strides in our understanding of the molecular makeup of DNA and RNA but missed out on the Nobel Prize.
Born in London on July 25, 1920, Franklin showed exceptional scholastic aptitude at an early age. After studying chemistry at Cambridge, Franklin went to work as a research associate at King's College London in the Medical Research Council's Biophysics Unit. During her tenure at King's College, she captured X-ray diffraction images of DNA that led to the discovery of the DNA's double helix. Her data was the basis for a 1953 hypothesis regarding the structure of DNA that led to the 1962 Nobel Prize.
Franklin died of ovarian cancer in 1958 at age 37 and was ineligible for Nobel Prize nomination in 1962. The honor was bestowed on Francis Crick, James Watson, and Maurice Wilkins based on their work contributing to the understanding of nucleic acids and not exclusively for their DNA structure discoveries. However, Crick wrote in 1961 that Franklin's data was "the data we actually used" to formulate their hypothesis on the structure of DNA.
While her exposure to X-ray radiation is sometimes linked to the illness that killed her, other members of her family have died of cancer.
Franklin's studies also contributed to the understanding of the molecular structures of viruses, coal, and graphite.
Born in London on July 25, 1920, Franklin showed exceptional scholastic aptitude at an early age. After studying chemistry at Cambridge, Franklin went to work as a research associate at King's College London in the Medical Research Council's Biophysics Unit. During her tenure at King's College, she captured X-ray diffraction images of DNA that led to the discovery of the DNA's double helix. Her data was the basis for a 1953 hypothesis regarding the structure of DNA that led to the 1962 Nobel Prize.
Franklin died of ovarian cancer in 1958 at age 37 and was ineligible for Nobel Prize nomination in 1962. The honor was bestowed on Francis Crick, James Watson, and Maurice Wilkins based on their work contributing to the understanding of nucleic acids and not exclusively for their DNA structure discoveries. However, Crick wrote in 1961 that Franklin's data was "the data we actually used" to formulate their hypothesis on the structure of DNA.
While her exposure to X-ray radiation is sometimes linked to the illness that killed her, other members of her family have died of cancer.
Franklin's studies also contributed to the understanding of the molecular structures of viruses, coal, and graphite.
marți, 7 mai 2013
AutoIt scripting increasingly used by malware developers
AutoIt, a scripting language for automating Windows interface interactions, is increasingly being used by malware developers thanks to its flexibility and low learning curve, according to security researchers from Trend Micro and Bitdefender.
"Recently, we have seen an uptick in the amount of nefarious AutoIt tool code being uploaded to Pastebin," Kyle Wilhoit, a threat researcher at antivirus vendor Trend Micro, said Monday in a blog post. "One commonly seen tool, for instance, is a keylogger. Grabbing this code, anyone with bad intentions can quickly compile and run it in a matter of seconds."
"In addition to tools being found on sites like Pastebin and Pastie, we are also seeing a tremendous increase in the amount of malware utilizing AutoIt as a scripting language," Wilhoit said.
The use of AutoIt in malware development has steadily increased since 2008, Bogdan Botezatu, a senior e-threat analyst at antivirus vendor Bitdefender said Tuesday via email. The number of malware samples coded in AutoIt has recently peaked at more than 20,000 per month, he said.
"In its early days, AutoIt malware was mostly used for advertising fraud or to create self-propagation mechanisms for IM [instant messaging] worms," Botezatu said. "Nowadays, AutoIt malware ranges from ransomware to remote access applications."
One particularly sophisticated piece of AutoIt-based malware discovered recently was a version of the DarkComet RAT (remote access Trojan program), Wilhoit said. This malware opens a backdoor on the victim's machine, communicates with a remote command and control server and modifies Windows firewall policies, he said.
The DarkComet RAT has been used in targeted, APT-style, attacks in the past, including by the Syrian government to spy on political activists in the country. What's interesting about the variant found by Trend Micro is that it's written in AutoIt and has a very low antivirus detection rate.
The use of scripting languages to develop sophisticated malware is not a widespread practice, because most of these languages require an interpreter to be installed on the machine or produce very large stand-alone executable files, Botezatu said.
However, there have been exceptions. For example, the Flame cyberespionage malware used the LUA scripting language to automate some tasks without being detected by antivirus products, Botezatu said.
AutoIt is extremely intuitive and easy to use, produces compiled binaries that run out of the box on modern Windows versions and is well documented, the Bitdefender researcher said. Also, there is already a lot of malicious AutoIt code available on the Web for reuse, he said.
"Most importantly, malware created in AutoIt is extremely flexible and can be easily obfuscated, which means that a single breed of malware written in AutoIt can be repackaged and re-crafted in a number of ways to prevent detection and extend its shelf life," Botezatu said.
As scripting languages like AutoIt continue to gain popularity, more malware developers are expected to migrate toward them, Wilhoit said. "The ease of use and learning, as well as the ability to post code easily to popular dropsites make this a great opportunity for actors with nefarious intentions to propagate their tools and malware."
Source:ITworld
Amazon adds to developer choices with JavaScript SDK for Web Services
The general release of the AWS (Amazon Web Services) SDK for Node.js is available for download, allowing developers to build server-side applications in JavaScript that then can run on Amazon's cloud.
The free SDK follows a preview version that Amazon announced in December last year. One of the advantages of Node.js is that developers can scale their applications without having to deal with polling, timeouts and event loops, according to Amazon. It is based on Google's V8 JavaScript engine and includes a library of functions that work under an event-driven model.
New features added to the generally available version include bound parameters, streams, IAM (identity and access management) roles for EC2 (Elastic Compute Cloud) instances, proxies and version locking. The latter feature allows users to lock into an API version for a service, which Amazon recommends if the API is relied on for production code. This way companies can isolate themselves from changes in updates of the SDK, it said.
Applications written using the SDK can be integrated with a long list of Amazon's cloud services, including Amazon's Relational Database Service and its Virtual Private Cloud offering, which lets users create logically isolated virtual servers and an optional VPN connection to their own data center.
Recently, Amazon also announced a version of Elastic Beanstalk for Node.js-based applications. Elastic Beanstalk aims to make it easier to quickly deploy and manage applications in Amazon's cloud. The tool can also be used with Java, PHP, Python, Ruby and .Net applications.
The preferred way to install the AWS SDK for Node.js is to use the npm package manager for Node.js, according to Amazon's documentation for the kit, which also includes a configuration guide and code examples.
Source:ITworld
Google hit by building automation security FAIL
The building housing Google Australia's lavish Sydney headquarters is running the known-vulnerable Tridium Niagara building management system, and has been compromised by the Cylance researchers who have made Niagara their mission.
The researchers identified the underlying system – QNX on an embedded system – and extracted the admin password from the system's config file. After that, as the company's blog post explains, they were able to wander around the control environment pretty much at will.
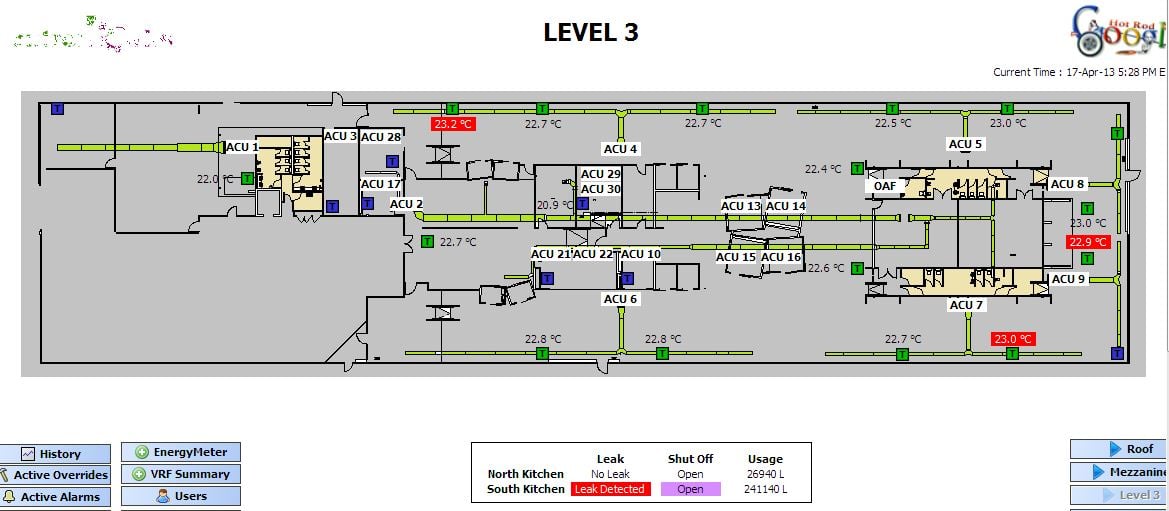
Billy Rios and Terry McCorkle demonstrate the successful attack by posting the building's Level 3 layout, water, and air-conditioning systems with the blog post. They also mention an “after hours button” they said they were “afraid to test” because of its hammer symbol in the system (hint: it probably merely activates the doors so people can get out after the doors have been switched off).
The Cylance gents admit that this vulnerability posting – which has been reported to Google – is linkbait in the service of awareness-raising.
At the time of this blog post, this exact issue affects tens of thousands of devices on the Internet and thousands of different organizations. Thank you Google for helping us raise awareness on this issue!” they write.
They noted that the Google vulnerability was present because the building in which the company resides was running an older version of the Niagara system, so there's likely to be a contractor with some explaining to do.
Source:Theregister
The researchers identified the underlying system – QNX on an embedded system – and extracted the admin password from the system's config file. After that, as the company's blog post explains, they were able to wander around the control environment pretty much at will.
Billy Rios and Terry McCorkle demonstrate the successful attack by posting the building's Level 3 layout, water, and air-conditioning systems with the blog post. They also mention an “after hours button” they said they were “afraid to test” because of its hammer symbol in the system (hint: it probably merely activates the doors so people can get out after the doors have been switched off).
The Cylance gents admit that this vulnerability posting – which has been reported to Google – is linkbait in the service of awareness-raising.
At the time of this blog post, this exact issue affects tens of thousands of devices on the Internet and thousands of different organizations. Thank you Google for helping us raise awareness on this issue!” they write.
They noted that the Google vulnerability was present because the building in which the company resides was running an older version of the Niagara system, so there's likely to be a contractor with some explaining to do.
Source:Theregister
Man Suspected of Developing and Distributing SpyEye Malware Extradited to the US
Hamza Bendelladj of Algeria, aka “Bx1,” has been extradited from Thailand – where he was arrested earlier this year while in transit from Malaysia to Egypt – to the US. He is accused of playing a critical role in developing, marketing, distributing and controlling the notorious piece of malware known as SpyEye.
The 24-year-old is charged with one count of conspiring to commit wire fraud and bank fraud, 10 counts of wire fraud, 11 counts of computer fraud, and one count of conspiracy to commit computer fraud.
If found guilty, he could spend up to 30 years in prison for conspiracy to commit wire and bank fraud, up to 5 years for conspiracy to commit computer fraud, up to 20 years for each wire fraud count, and up to 5 or 10 years for each count of computer fraud.
In addition, he could be forced to pay fines totaling $14 million (€10.6 million).
According to the US Department of Justice, between 2009 and 2011, Bendelladj and others allegedly developed, marketed and sold versions of SpyEye to other cybercriminals.
Authorities believe that Bendelladj also operated command and control (C&C) servers for the SpyEye malware.
“No violence or coercion was used to accomplish this scheme, just a computer and an Internet connection. Bendelladj’s alleged criminal reach extended across international borders, directly into victims’ homes,” said US Attorney Sally Quillian Yates.
“In a cyber-netherworld, he allegedly commercialized the wholesale theft of financial and personal information through this virus which he sold to other cybercriminals. Cybercriminals take note; we will find you. This arrest and extradition demonstrates our determination to bring you to justice.”
FBI Special Agent in Charge Mark F. Giuliano of the Atlanta Field Office commented, “The FBI has expanded its international partnerships to allow for such extraditions of criminals who know no borders.”
He added, “The federal indictment and extradition of Bendelladj should send a very clear message to those international cyber-criminals who feel safe behind their computers in foreign lands that they are, in fact, within reach.”
Source:Softpedia
Syrian Electronic Army Hacks “The Onion” Twitter and Facebook Accounts
Hackers of the Syrian Electronic Army have hijacked the social media accounts of yet another news organization. Their latest victim is The Onion, the famous American news satire organization.
The hackers say they’ve hijacked a total of five Twitter accounts – TheOnion, OnionSports, ONN, TheAVClub and OnionPolitics –, and two of the publication’s Facebook accounts.
“Syrian Electronic Army Hacked today Twitter accounts and Facebook pages of The Onion satirical newspaper. And that came after that website published a news that harms the reputation of Syria and its leader,” the hackers wrote on their website.
SyriaNews has caught a glimpse of the messages published by the pro-Assad hackers from the compromised accounts.
“UN’s Ban Ki Moon condemns Syria for being struck by israel: ‘It was in the way of Jewish missiles’,” one of the tweets read.
“UN retracts report of Syrian chemical weapon use: ‘Lab tests confirm it is Jihadi body odor’,” the hackers wrote.
Shortly after recovering their accounts, representatives of The Onion have confirmed the incident, in their own manner.
“Following today’s incident in which the Syrian Electronic Army hacked into The Onion’s Twitter account, sources at America’s Finest News Source confirmed that its Twitter password has been changed to OnionMan77 in order to prevent any future cyber-attacks,” reads an article published on The Onion shortly after the breach.
The Onion has published several satirical posts related to the incident, including “The Onion’s tips on how to prevent your major media site from being hacked” and “Syrian Electronic Army has a little fun before inevitable upcoming deaths at hands of rebels.”
In addition to compromising The Onion’s social media accounts, the Syrian Electronic Army also appears to have hijacked the email accounts of at least a couple of staff members
Source:Softpedia
The hackers say they’ve hijacked a total of five Twitter accounts – TheOnion, OnionSports, ONN, TheAVClub and OnionPolitics –, and two of the publication’s Facebook accounts.
“Syrian Electronic Army Hacked today Twitter accounts and Facebook pages of The Onion satirical newspaper. And that came after that website published a news that harms the reputation of Syria and its leader,” the hackers wrote on their website.
SyriaNews has caught a glimpse of the messages published by the pro-Assad hackers from the compromised accounts.
“UN’s Ban Ki Moon condemns Syria for being struck by israel: ‘It was in the way of Jewish missiles’,” one of the tweets read.
“UN retracts report of Syrian chemical weapon use: ‘Lab tests confirm it is Jihadi body odor’,” the hackers wrote.
Shortly after recovering their accounts, representatives of The Onion have confirmed the incident, in their own manner.
“Following today’s incident in which the Syrian Electronic Army hacked into The Onion’s Twitter account, sources at America’s Finest News Source confirmed that its Twitter password has been changed to OnionMan77 in order to prevent any future cyber-attacks,” reads an article published on The Onion shortly after the breach.
The Onion has published several satirical posts related to the incident, including “The Onion’s tips on how to prevent your major media site from being hacked” and “Syrian Electronic Army has a little fun before inevitable upcoming deaths at hands of rebels.”
In addition to compromising The Onion’s social media accounts, the Syrian Electronic Army also appears to have hijacked the email accounts of at least a couple of staff members
Source:Softpedia
vineri, 3 mai 2013
State of Louisiana Website Hacked, Spreads Sirefef Malware
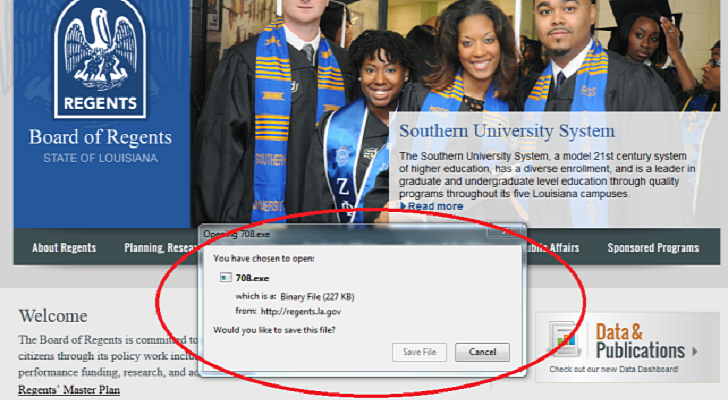
The official website of the Board of Regents of the State of Louisiana (regents.la.gov) has been hacked and abused to distribute a variant of the notorious Sirefef malware.
Avast reports that the malware is hosted in the “wp-content” folder of the site and it’s served as an executable to anyone who visits a specific URL. It’s likely that the cybercriminals use spam to distribute the malicious links.
Once infected, computers become part of a peer-to-peer botnet. Such botnets are difficult to disrupt because they don’t have a main communication node that can be disconnected.
This particular botnet has already infected over 300,000 devices, but the number of infection attempts exceeds 800,000.
By compromising the websites of high-profile organizations, cybercriminals increase their campaigns’ chances of success. That’s because many users will likely click a link that appears to point to a .gov website without giving it too much thought.
I've checked the website and, unfortunately, at the time of writing, it still hosted the malware.
Additional technical details of this attack are available on Avast’s blog.
Source:Softpedia
Website of Iran’s Basij Force Taken Down by Cyberattacks
As the presidential elections draw near, tension mounts in Iran both in the real world and in cyberspace. On May 1, the official website of the country’s Basij military branch was taken down after a cyberattack was launched against it.
“Due to the impending vote, elements of the global arrogance have launched a new round of cyberattacks against Basij websites, particularly Basij.ir,” the force’s representatives stated according to Think Progress.
A spokesman revealed that the Basij website had faced numerous attacks over the past three years.
In the meantime, members of the Iranian hacktivist group Ashiyane Digital Security have told Softpedia they’re preparing an operation against governments and media organizations that have spread lies about Iran.
“Our mission is protect Iran from hackers & social media lies,” the group’s leader said.
“They don’t know the truth and when the government lies we will try to take them down. When Social Media lies we will try to take them down,” he added.
Source:Softpedia
New Avast Update Includes VPN Service
The fresh update released by AVAST for version 8 of their product line adds VPN service to the suites.
VPN component in avast! products offers users the possibility to browse anonymously and securely since all communication is encrypted. This type of browsing is particularly handy when connecting to the Internet from a public place, through Wi-Fi.
Dubbed SecureLine, the new service is not free, but a 24-hour test period is available. The price for this service is $7.99/6EUR for one month, and you can also get the package for one year ($59.99/45.73 EUR).
Additional modifications present in this revision refer to improvements that touch on stability and performance. Compatibility with screen readers has also been enhanced as well as the update mechanism.
Source:Softpedia
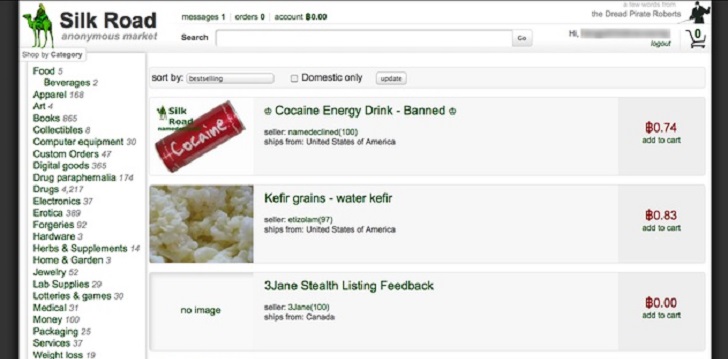
Famous Underground Marketplace Silk Road Hit by DDOS Attack
Silk Road, the notorious underground market that’s known for selling drugs and other illegal goods, has been disrupted over the past few days due to a distributed denial-of-service (DDOS) attack.
The Silk Road is highly popular among criminals because it’s only accessible via the Tor anonymity network and it uses Bitcoin to protect its customers’ privacy.
The reasons behind the attack are uncertain, but there are two main theories.
News.com.au reports that someone is trying to blackmail the site’s administrator into paying a $5,000 (€3,800) ransom.
However, according to Bitcoin Magazine, none of the posts published by Silk Road’s administrator mention anything about blackmail.
The second theory is that someone might be launching a similar service and wants to take out the competition.
Silk Road’s administrator, who calls himself Dread Pirate Roberts, reveals in a post that they “still do not have the upper hand” in the battle. He explained that it might take the restructuring of the Tor software or even the Tor network to mitigate the attack.
In the meantime, he’s considering an alternative semi-private scheme that would allow users to access the service via “many private URLs.”
Source:Softpedia
Beijing Prosecutors Lack Skills to Investigate Cybercrimes
While Chinese hackers are considered to be among the best in the world, the country’s prosecutors are not very skilled when it comes to investigating online criminal activities. That’s why, prosecuting authorities in Beijing plan on hiring and training more individuals capable of analyzing electronic evidence.
People’s Daily reports that most prosecutors don’t have a technical background and lack the necessary knowledge to investigate online fraud and other crimes.
In the past 5 years, Beijing’s Chaoyang district handled over 50 cases of fraud that leveraged the Web. Authorities from the Shijingshan district prosecuted more than 200 individuals involved in such crimes.
In 2012, Beijing started training prosecutors to enhance their computer skills. However, currently, there are less than 10 individuals who are good at their job.
To address this gap, more prosecutors will be trained, but Beijing People's Procuratorate also plans on hiring individuals with a background in computers and networks.
Source:Softpedia
Indian Politicians Hire Hackers to Spy on Their Opponents
Some Indian politicians have stopped using their smartphones for important communications after news broke out that hackers were being hired by their political opponents.
Times of India reports that hackers and security experts are being offered Rs 1 lakh ($1,852 / €1,416) and sometimes even more to breach the smartphones of ministers, members of the legislative assembly and members of parliament.
N Nityanand, CTO of Entersoft Information systems at Ameerpet, says that he has been approached on numerous occasions and offered as much money as he wanted to break into the email accounts of top politicians. Nityanand has refused for ethical reasons, but not everyone is like him.
Usually, the hackers are contacted by mediators of the political leaders who don’t name the individuals they represent. They want to be able to intercept phone calls, text messages, emails and anything else that might be of interest.
To gain control of the smartphones of politicians, the hackers send out emails that point to cleverly designed websites. When the links from the emails are clicked, a malicious software is downloaded onto the device.
Source:Softpedia
Adobe to Fix PDF Information Leakage Issue on May 14
A few days ago, researchers from security firm McAfee reported uncovering a PDF usage tracking issue in Adobe Reader. The flaw can be leveraged by an attacker to track when and where PDF documents are opened.
Adobe says it’s aware of the issue, which it catalogues as being of “low severity.”
“A user’s IP address and timestamp could be exposed when opening a specially crafted PDF and then clicking a URL within the document,” Adobe’s PSIRT wrote in a blog post.
The company says it will address this bug in both Reader and Acrobat with the next scheduled release, on May 14.
McAfee experts have admitted that the vulnerability is not critical, but they have warned that it could be leveraged in the first phase of sophisticated attacks.
Source:Softpedia
BlackBerry 10 passes US defence department tests
BlackBerry has secured access to a critical market – the US military – for its new operating system and handsets and version 10 of its Enterprise Service software.
Sighs of relief at the news may well be rattling the windows at BlackBerry's headquarters, because the company has staked its future on secure messaging. Winning approval for BlackBerry 10 devices to be used on US Department of Defense networks means the company has a chance of winning business at a colossal customer and can also tell world+dog all about its certification whenever it tries to sell secure messaging elsewhere.
The company is, understandably, crowing about the win and its place on the Unified Communications Approved Product List (UCAPL) maintained by the Defense Information Systems Agency. The content of that crowing is a little curious, as a canned statement from Scott Totzke, a senior veep for security at BlackBerry says “This approval will enable DoD customers to connect their BlackBerry Z10 or BlackBerry Q10 smartphones to DoD networks and securely access assets from work, while enjoying the wealth of consumer-oriented functionality that BlackBerry 10 brings to market.”
Whether Totzke was referring to the "Balance" feature of BB10 that creates a walled garden to facilitate BYOD or a scenario in which military personnel will use generic BlackBerry messaging apps while also being able to use Angry Birds was not explained. On balance, one imagines Totzke was referring to Balance, a suggestion we offer while we wait for BlackBerry to appear on the UCAPL, which at the time of writing mentioned only BlackBerry products from RIM.
The certification applies to both the Q10 and Z10 handsets and the PlayBook tablet.
Source:theregister
IBM open sources new approach to crypto
A group of IBM researchers has released a Github project that implements a homomorphic encryption system – a way to work on encrypted data in a file without first decrypting the whole file.
Why would anyone want to do that? Partly because if you have to decrypt the file to work on it, it's going to exist as plaintext somewhere. IBM has other ideas about this as well: leaving the encrypted file encrypted would keep data protected in the cloud while still letting users work on it. Big Blue even envisages such schemes as offering truly private Internet search.
The Github project is called HElib – the homomorphic encryption library. Its authors describe it as “an implementation of the Brakerski-Gentry-Vaikuntanathan (BGV) scheme, along with many optimizations to make homomorphic evaluation runs faster, focusing mostly on effective use of the Smart-Vercauteren ciphertext packing techniques and the Gentry-Halevi-Smart optimizations.”
The challenge is getting it to run efficiently, something described by IBM's Craig Gentry in 2009, and improved upon in later work.
In addition to algorithms for key generation, encryption, and decryption, the homomorphic scheme adds an “Evaluate” function.
The encrypted file – if The Register understands the paper correctly – embeds actions that are permitted on that file (for example, the ability to read and write to parts or all of the file. The Evaluate function is able to use the combination of the public key and permitted actions (described as circuits) to operate on the file without decrypting it.
Source:TheRegister
Supersize your free cloud storage to 100GB or more
Just a few short years ago, cloud storage services that synced files and folders across multiple PCs and mobile devices were just a dream. But thanks to the rapid rise of entities like Dropbox, SugarSync, and Google Drive, cloud storage and syncing services are nearly ubiquitous today, acting as hard drives in the sky that help you do all kinds of things--such as creating a bulletproof (almost) backup system or turbocharging your productivity to blistering new levels--no matter where you are.
If you have the space, that is. Truly wondrous setups require robust cloud storage capabilities, but that doesn't mean you have to drop dollars for extra gigs.
Most services offer free accounts with modest quantities of complimentary cloud storage. In isolation, these pittances don't amount to much, but merged into Voltron-like unity, the free storage from several services can achieve mammoth totals. With some patience, you can build your own supercloud with more than 100GB of free storage. With a lot of patience (and pestering of your pals), you can nab more than 225GB. And all that online storage is free-as-in-free-beer free.
Here's how to do it, along with some tips on how to manage your storage hoard to take advantage of each service's unique properties.
Getting started
Setting up a personal supercloud can be tedious, depending on how many such services you already use. Your first step should be to grab all of the services that install dedicated areas in the Favorites column of Windows Explorer.
Amazon Cloud Drive: 5GB
Box: 5GB (but read "Beyond referrals" below before installing Box, as you may want to postpone installing this one)
Dropbox: 2GB
Google Drive: 5GB
MiMedia (m)Drive: 7GB
SkyDrive: 7GB (longtime SkyDrive users may be eligible for 25GB free)
SpiderOak: 2GB
Storage subtotal to this point: 33GB
Now install SugarSync, which assigns itself a virtual drive letter--à la the C: or D: drive--instead of a customized folder. SugarSync offers 5GB free to start.
Next, install the two cloud services that use a desktop app to sync and store files instead of creating a folder in Windows.
MediaFire: 10GB
Ubuntu One: 5GB
Storage subtotal to this point: 53GB
Finally, open an account at the notorious Mega.co.nz to grab a whopping 50GB of free online cloud storage. Mega doesn't offer multiple device syncing. Instead, it functions more as an in-browser, Box-like storage locker. The service expects to add mobile apps and accompanying device syncing at some future date, but those options aren't available today.
Tip: Both SpiderOak and Mega currently use encryption schemes that make recovering your password impossible. If you forget your password for either service, you'll lose access to your files permanently. We strongly recommend that if you have a hard time remembering passwords, you give the LastPass password manager a whirl.
Just like that, your supercloud has mushroomed to an impressive 103GB. Now let's look at some ways to get even more storage.
Refer your friends to get more storage
Several cloud services offer extra storage in 500MB increments for every friend that you refer to it, but the maximum amount of free storage they permit under these bounty programs varies. Dropbox lets you add up to 16GB via referrals, while Ubuntu One tops out at 20GB of extra space, and SugarSync allows up to 32GB of additional storage in half-gig chunks. Note that Dropbox requires each referred user to join Dropbox, install the service's desktop app, and sign in to the desktop app after installation.
MiMedia offers you an additional 1GB of storage for every five friends you sign up, with a ceiling of 5GB of extra space from such referrals.
SpiderOak and MediaFire are a bit more generous, offering 1GB of additional free storage for each referral, to a maximum of 10GB and 32GB, respectively.
Beyond referrals
An easier way to increase the amount of free Dropbox storage available to you is to install the Dropbox app for Android or iOS, and then authorize automatic photo uploads from your device. Once authorized, the Dropbox mobile app will automatically begin uploading all photos snapped on your device to Dropbox. Dropbox doles out an extra, permanent 500MB to your account, as you need it, until you reach 3GB worth of free picture-driven storage.
Dropbox also presents you with 250MB of free space for completing its Getting Started tutorial.
SugarSync gives users a few ways to acquire extra free storage in 125MB chunks: You can install the mobile app for Android, BlackBerry, or iOS; or share a file or folder with a public link, or a folder with a private link; or upload a file to your account via email.
MediaFire rewards you with 2GB for installing the MediaFire desktop, and 2GB more for installing mobile apps. Connecting your Facebook and Twitter accounts to MediaFire fetches you another 1GB each. And if you spam your social networks about MediaFire, you receive another 1GB of storage.
Box doesn't have a referral program, but the company often offers 50GB of free storage to new users. Following the company on Facebook is a good way to find out quickly when the next 50GB giveaway is about to happen.
Both Google Drive and Microsoft offer free storage as an add-on when you make certain purchases. If you buy selected Chrome OS devices, Google will dole out either 1TB or 100GB of extra free Google Drive storage space for a limited time. Google maintains a list of Chromebook storage deals here. Microsoft offers an additional 20GB of SkyDrive storage to Office 365 Home Premium subscribers. Annual subscriptions to the Office suite cost $100 per year.
Not including the offers from Box, Google, and Microsoft, the referral and social media credits listed here could help industrious and methodical gleaners snag another 126GB of free cloud storage. But once you've accumulated all that space, how do you use it effectively? The key to maximizing your use of a vast mound of fractured cloud storage is to match what you commonly do with cloud storage to each service's strengths and weaknesses.
General sharing and sync
Once you've beefed up its storage total, Dropbox should be your service of choice for file syncing, thanks to its unparalleled platform support and widespread use. Box, SpiderOak, SkyDrive, and MediaFire are solid options, too. SugarSync lets you choose specific folders to sync, rather than forcing you to dump all of your files into a central location, and that feature may appeal to some people.
For sensitive documents, you'll want to use SpiderOak, which advertises fully encrypted, zero-knowledge online data backup (and sync). It's rock-solid.
For less sensitive material that nonetheless requires encryption, you could use Mega. Security researchers recently called Mega's encryption scheme into question, and Mega founder Kim Dotcom is not beloved in law enforcement circles, but even so it offers more protection than typical cloud services do. Just make sure that you have backups handy in case Mega goes the way of Megaupload.
Online collaboration
Google Drive is your best bet if you need to edit a document online with one or more people. Google Drive features robust editing features, thanks to its integration with Google Docs, including multiuser, simultaneous editing. Since millions of people rely on Google services, most of the people you need to work with probably use Google Docs. You can edit documents with Google's mobile apps for Drive on Android and iOS.
A second choice would be Microsoft's SkyDrive. Microsoft offers free Web-based versions of its well-known Office suite, including apps for Word, Excel, OneNote, and PowerPoint. Office Web apps often experience technical hiccups, however, and the Word Web app doesn't have an autosave feature--so you risk losing work if you forget to save. The collaboration features aren't as seamless as Google's, either. For example, both writers must save to see the other person's changes when collaborating on a Word doc.
Box offers online document editing as well as Web-based integration with Google Docs.
Media
The natural choice for streaming music is Amazon's Cloud Drive, but the company recently separated its cloud storage and cloud music services. Dropbox offers music streaming through its mobile apps, but it will play only one song at a time. In December, Dropbox acquired Audiogalaxy, a music streaming service, prompting many observers to speculate that a Dropbox-powered music feature is on the way.
MiMedia offers media streaming, but I can't recommend it for that purpose. In my tests, MiMedia choked when uploading videos as small as 18MB. Also, using MiMedia's Dropbox-style folder on Windows 8 caused Windows Explorer to hang repeatedly, a problem I didn't encounter with any of the other cloud services.
If you want to stream music online, a good choice is SugarSync, which offers music streaming as part of its service. You could also just stick with Google Music (not previously mentioned, as it doesn't offer traditional storage), which lets you upload 20,000 tracks from your personal music library and stream them from any online location you can reach.
For online video streaming, you can use Jolidrive (see below).
Backups and cold storage
SpiderOak and Ubuntu One let users backup specific folders to the cloud. MiMedia's desktop application also works well for folder-specific backups, which don't rely on manual uploads or file manipulation.
Box and Mega are ideal for storing files that you rarely access but want to keep in the cloud, especially if you can snag one of Box's 50GB free introductory deals. You can also use Mega's 50GB of free storage to store ample wares--but again, don't rely exclusively on Mega for file storage. It might go away.
Bringing it all together
Managing multiple cloud services can be a pain, even with widespread Windows Explorer integration. Fortunately, you don't have to handle the job on your own: Jolidrive from Jolicloud creates a cloud services dashboard that displays your Box, Dropbox, Google Drive, SkyDrive, SugarSync, and Ubuntu One files in one location. Jolidrive is especially helpful when you're on a public PC and you need access to your cloud files.
The service adds a few handy features of its own, such as music and video streaming, Google Drive document editing, and integration with Pocket and Instapaper. You can also connect various social networks--including Facebook, Google+, and Tumblr--to Jolicloud to view your social feeds in a Pinterest-style layout.
Jolicloud doesn't offer a way to transfer files between cloud services. A similar service called Otixo does provide that functionality, but Otixo no longer offers a free version of its service, alas.
And that's that. Welcome to your fully functional and uber-flexible hard drive in the cloud! Now, how to fill all that free space...
Source:IT World
Acer introduces $169 Android tablet
Acer has placed its bet in the tablet wars on low pricing, introducing a US$169 Android tablet with a 7.9-inch screen.
The Iconia A1 is full-featured, has an "accessible" price and will raise the stakes in the tablet wars, said Jim Wong, president of Acer, during a speech at a press event in New York on Friday morning.
The tablet offers more than eight hours of battery life and an IPS display, also found on iPads. The tablet also has a quad-core processor, which is likely based on an ARM design. Shipment information for the product was not immediately available.
With the Iconia A1, Acer is entering a highly competitive low-cost tablet market, with vendors lowering prices as a way to gain market share. Acer's new tablet comes just a few days after Hewlett-Packard started shipped the $169.99 Slate 7, which has a 7-inch screen and dual-core processor, but misses many basic features like GPS. Acer's tablet has a larger screen and an equivalent processor to Google's Nexus 7, which has a 7-inch screen and the latest version of Android.
At the event, Acer also introduced new laptops, brought in New York-based artists and musicians to help showcase the products.
Acer introduced the Aspire R7 hybrid, which has a screen that can be folded in a variety of ways. The 15.6-inch screen hinge can extend up in the same plane as the keyboard like an all-in-one touch desktop. The hybrid device's screen can also be flipped around and laid flat over a keyboard for the device to become a tablet. The product will become available worldwide on May 14 through retail channel partners in the U.S. and worldwide. Pricing was not immediately available.
Acer also introduced the P3 hybrid ultrabook, which functions as a tablet and ultrabook. The device's screen can be pulled out from a keyboard to operate independently as a tablet. The P3 will run on Intel's processors.
Acer's PC shipments have been falling over the last few quarters, and it is now the fourth largest PC maker in the world.
The company's PC market share started tumbling as people moved to tablets and left behind netbooks, a market in which Acer was a leader.
"The last couple of years we saw this won't carry us to the next stage," said Wong. The company is ready to move into a new era of tablets and hybrids, he added.
Acer projects second-quarter sales of Windows 8 laptops and hybrids to be double that of first quarter, said JT Wang, Acer's chairman and CEO. There is growing acceptance of Windows 8 devices that can function as laptops and tablets with touch capabilities and keyboards, he said.
Wang took a shot at Apple's iOS, saying consumers will reject being controlled by operating systems and devices.
Source:IT World
Gmail users can now automatically generate Calendar entries
Google has started rolling out a new feature in Gmail that lets users create Google Calendar entries from their email messages.
Gmail now detects dates and times in the text of email messages and highlights them. Users can click on the highlighted text and trigger a pop-up box for configuring a Calendar item.
The process of creating and modifying the Calendar item happens within Gmail. The Calendar entry will automatically contain a link back to the email from which it was created.
The new feature is being delivered over the coming week to all individual users of Gmail's English-language version, as well as to organizations that use Gmail as part of the broader Google Apps cloud suite. This rollout schedule excludes Google Apps customers who have opted to receive application updates at longer intervals.
Google plans to add the feature to non-English versions of Gmail later on, the company said in a blog post.
The feature is intended to increase the convenience of using Calendar, which has historically not been as well regarded by users as Gmail, by far the most popular of Google's communication and collaboration applications.
By more tightly tying Gmail and Calendar, Google is increasing its efforts to lure users of Microsoft Outlook, the ubiquitous email and calendar desktop application that is often used in conjunction with Gmail as a backend email server by Apps customers. Google would like all Apps customers to use the Gmail and Calendar web interfaces, instead of the Outlook client.
People's attachment to Outlook has been a stumbling block for Google as it pushes Apps as an alternative to the Microsoft Office productivity applications and servers, like Exchange and SharePoint. In some cases, employees' preference for Outlook has derailed efforts to implement Google Apps in organizations.
Source:ITNews
Samsung Galaxy S4 earns Pentagon security nod
The Pentagon gives official approval to any Samsung device protected by the Knox security software, which for now includes just the Galaxy S4.
Samsung's Galaxy S4 has been approved for government use.
(Credit: Sarah Tew/CNET)
Samsung is now clear to start pitching its new flagship phone to the government.
The handset maker announced Friday that its Knox-enabled mobile devices have been approved by the Pentagon for government use. Samsung's Knox software offers high-level encryption, a VPN feature, and a way to separate personal data from work data. The software also enables IT administrators to manage a mobile device through specific policies.
For now, the Galaxy S4 is the only Samsung device equipped with Knox. But the company promises that other smartphones as well as tablets will receive the security software.
The thumb's up from the Pentagon means that the S4 and future Knox devices can be used by U.S. government and military departments that tap into the Department of Defense networks. Access to these networks requires high security standards, and the S4 is the first Android phone to meet the requirements, according to Samsung.
The new security clearance also opens up certain types of businesses as potential new customers for Samsung.
"We are very pleased to announce that the U.S. Department of Defense has approved Samsung Knox-enabled devices for use in DoD networks," Samsung Mobile President JK Shin said in a statement. "This approval enables other government agencies and regulated industries such as health care and financial services to adopt Samsung Galaxy smartphones and tablets. This is a significant milestone for Samsung as we work to grow our relationships within government and large corporate enterprises."
On Thursday, the Pentagon gave the same approval to BlackBerry devices with the BlackBerry 10 operating system, which translates into its Q10 and Z10 smartphones and Playbook tablets.
In the past, BlackBerry was the go-to vendor for government and big business due to the high-level security on its devices. But Apple and Android have begun carving out of a chunk of this lucrative market. Samsung in particular is aiming to muscle in on BlackBerry's territory with help from its Knox software.
Part of the Samsung for Enterprise (SAFE) initiative, Knox comes built into the operating system and addresses all major security holes in Android, according to the company. Knox's ability to keep personal and business data separate matches a similar feature in BB10 called BlackBerry Balance.
Up to now at least, BlackBerry hasn't appeared to be concerned about Samsung's efforts.
"Whatever any of our competitors announce, one thing won't change. The most secure mobile computing solution is a BlackBerry device running on a BlackBerry platform," David Smith, executive vice president of mobile computing for BlackBerry, said in February.
The government's nod to both Samsung and BlackBerrry still leaves Apple out in the cold.
The iPhone maker is also seeking approval from the Department of Defense for its mobile devices. Specifically, the DOD needs to certify the iOS 6 operating system as secure enough to be used by defense agencies and the military. However, that approval is expected within the next few weeks, The Wall Street Journal reported Wednesday.
Passing the government's security test doesn't automatically guarantee a sale. Approvals "do not directly result in product orders, but facilitate the process by eliminating the need for security reviews at the individual DOD organization level," a Defense Department spokesman told the Journal.
Samsung, BlackBerry, and potentially Apple will still need to fight over lucrative government contracts just as they do in the business world. But assuming Apple does win security approval, all three rivals will duke it out on an even playing field.
Source: Mobile
Samsung's Galaxy S4 has been approved for government use.
(Credit: Sarah Tew/CNET)
Samsung is now clear to start pitching its new flagship phone to the government.
The handset maker announced Friday that its Knox-enabled mobile devices have been approved by the Pentagon for government use. Samsung's Knox software offers high-level encryption, a VPN feature, and a way to separate personal data from work data. The software also enables IT administrators to manage a mobile device through specific policies.
For now, the Galaxy S4 is the only Samsung device equipped with Knox. But the company promises that other smartphones as well as tablets will receive the security software.
The thumb's up from the Pentagon means that the S4 and future Knox devices can be used by U.S. government and military departments that tap into the Department of Defense networks. Access to these networks requires high security standards, and the S4 is the first Android phone to meet the requirements, according to Samsung.
The new security clearance also opens up certain types of businesses as potential new customers for Samsung.
"We are very pleased to announce that the U.S. Department of Defense has approved Samsung Knox-enabled devices for use in DoD networks," Samsung Mobile President JK Shin said in a statement. "This approval enables other government agencies and regulated industries such as health care and financial services to adopt Samsung Galaxy smartphones and tablets. This is a significant milestone for Samsung as we work to grow our relationships within government and large corporate enterprises."
On Thursday, the Pentagon gave the same approval to BlackBerry devices with the BlackBerry 10 operating system, which translates into its Q10 and Z10 smartphones and Playbook tablets.
In the past, BlackBerry was the go-to vendor for government and big business due to the high-level security on its devices. But Apple and Android have begun carving out of a chunk of this lucrative market. Samsung in particular is aiming to muscle in on BlackBerry's territory with help from its Knox software.
Part of the Samsung for Enterprise (SAFE) initiative, Knox comes built into the operating system and addresses all major security holes in Android, according to the company. Knox's ability to keep personal and business data separate matches a similar feature in BB10 called BlackBerry Balance.
Up to now at least, BlackBerry hasn't appeared to be concerned about Samsung's efforts.
"Whatever any of our competitors announce, one thing won't change. The most secure mobile computing solution is a BlackBerry device running on a BlackBerry platform," David Smith, executive vice president of mobile computing for BlackBerry, said in February.
The government's nod to both Samsung and BlackBerrry still leaves Apple out in the cold.
The iPhone maker is also seeking approval from the Department of Defense for its mobile devices. Specifically, the DOD needs to certify the iOS 6 operating system as secure enough to be used by defense agencies and the military. However, that approval is expected within the next few weeks, The Wall Street Journal reported Wednesday.
Passing the government's security test doesn't automatically guarantee a sale. Approvals "do not directly result in product orders, but facilitate the process by eliminating the need for security reviews at the individual DOD organization level," a Defense Department spokesman told the Journal.
Samsung, BlackBerry, and potentially Apple will still need to fight over lucrative government contracts just as they do in the business world. But assuming Apple does win security approval, all three rivals will duke it out on an even playing field.
Source: Mobile
Ericsson sees tough fight in Chinese 4G, brighter signs elsewhere
STOCKHOLM (Reuters) - Ericsson expects cut-throat competition between telecoms equipment makers as China prepares to spend billions of dollars on high-speed networks, punishing margins at a time when profitability is already under pressure.
A decade-long price war launched by Chinese vendors Huawei and ZTE has already forced suppliers like Nortel and Motorola out of the market while smaller players like Alcatel-Lucent are mired in losses.
Equipment makers hoping the roll-out of 4G - also known as LTE - networks in China later this year will ease industry problems will be disappointed.
Projects to roll out networks across a country tend to have a higher proportion of hardware to software content and are less profitable than projects to upgrade existing networks, which have the opposite mix.
"It is a new coverage project to deploy LTE and of course we know ... coverage projects have lower profitability," Johan Wibergh, head of Ericsson's Networks unit, told Reuters earlier this week.
China's three mobile operators - China Mobile, China Unicom and China Telecom - plan to spend a combined 345 billion yuan ($56 billion) this year on network upgrades and 4G.
China Mobile plans to plough 41.7 billion yuan ($6.75 billion) this year into 200,000 4G base stations in order to provide services for its 710 million customers - more than twice as many as there are people in the U.S.
Wibergh said such flagship projects would attract fierce competition from vendors, including China's domestic giants Huawei - the world's second biggest vendor after Ericsson - and ZTE.
Outside China, however, Wibergh saw some relief from years of price pressure and said the company had raised its prices in 2012, though not by much.
Struggling vendors have less appetite now for margin-sapping price wars, he added.
"I think the worst is behind us," he said. "I think everyone needs some kind of stability in this industry."
(Reporting by Simon Johnson; Editing by Sophie Walker)
Source: Reuters
How Twitter fueled a market swoon
A fake report posted by hackers on the Associated Press Twitter feed caused the S&P 500 to drop 0.9 percent
A single tweet can be enough to cause a stock market crisis, says Christopher Matthews at TIME. We learned that last week, when hackers posted a fake report on the Associated Press Twitter feed claiming that Barack Obama had been injured in an explosion at the White House. The AP quickly flagged the tweet as fake, but not before it "sent shock waves through the market," causing the S&P 500 to drop 0.9 percent and temporarily wiping out $136 billion in stock value. The real culprit behind this latest "flash crash" isn't a hacker — it's "the proliferation of high-frequency trading." Wall Street firms use computer algorithms to make millions of trades per second, triggered by automated scans of news sources- — including Twitter — for specific words or phrases. They make money, but "when the going gets tough, these computers tend to sell quickly and run for the hills, actually reducing liquidity when the market needs it most."
Don't blow this out of proportion, say Jared Keller and Evan Applegate at Businessweek. Cases of false tweets and news reports wreaking havoc on the markets are rare. In 2011, for instance, Apple shares dipped just 1 percent (and quickly rebounded) after a false report said that Apple founder Steve Jobs had died. And when a Twitter account impersonating prominent short-seller David Einhorn tried to "induce fluctuations" in Herbalife's stock in February, the company's value underwent "no noticeable change." Still, the AP episode "highlights the potential pitfalls of relying on social networks for tradable information," especially on the heels of the Securities and Exchange Commission's announcement that companies can use social media sites, including Twitter and Facebook, "to share market-moving company announcements."
The solution is better security, says Caleb Garling in the San Francisco Chronicle. The First Amendment "prevents the government from controlling what users say on Twitter," but regulators can make social media firms beef up their protocols. False information "has the potential to be damaging to more than the financial world." Just imagine: "If the hacked AP tweet had been more believable and not as easy to discredit — say, 'U.S. Navy moving into strategic positions around North Korea' — a global emergency could have ensued." The technology sector may disdain regulation, but "other kinds of information, such as financial and health-care data, are already strictly regulated by law." It's up to the consumer to decide what to trust on Twitter, but messages shouldn't be so easy to fake.
"Other than self-restraint, which is in short supply these days, nothing much can be done to prevent any of this," says George Packer at The New Yorker. Social media sites will seek new means to "spread information, for better and worse, farther and faster than the Spanish flu." And unless regulators crack down on high-frequency traders, they "will go on using algorithms that turn milliseconds of information advantage into huge profits" — even if that information is wrong.
New Zealand's internet bad boy wants to see top U.S. lawman
WASHINGTON/WELLINGTON (Reuters) - A trip to New Zealand will put America's chief prosecutor on the same soil as a flashy internet mogul who is fighting extradition to the United States on charges he assisted massive piracy of copyrighted movies and music.
U.S. Attorney General Eric Holder visits New Zealand next week for an annual meeting of a "quintet" of attorneys general from mostly English-speaking countries - and not to meet up with the entrepreneur Kim Dotcom.
The founder of defunct file-sharing service Megaupload, Dotcom has oscillated between assailing Holder's trip and wanting to hear what he has to say in person.
It was unclear on Thursday whether Holder would appear in public. His speech at the University of Auckland is planned primarily for students and will be closed to the public and the media, although his U.S. speeches are usually open to the media.
In Twitter posts, Dotcom requested a ticket to the speech, offered to send T-shirts and an ethics manual to wherever Holder is staying and challenged his followers to film Holder while a Megaupload theme song plays for a $500 prize.
Dotcom tweeted that he would like to understand Holder's definition of cybercrime, one issue the quintet works on.
An extradition hearing for Dotcom is scheduled for August, although appeals could further delay it, said Ira Rothken, a lawyer for Megaupload. He told Reuters by phone he had no reason to expect a meeting between Holder and Dotcom.
Holder declined an interview through a spokeswoman on Thursday. Federal prosecutors in Virginia who are handling the case declined to comment on how it is proceeding.
Dotcom got rich from founding Megaupload, which allowed users to upload and download movies, music, television shows, e-books and software. The site once commanded 4 percent of global online traffic before U.S. prosecutors shut it down.
The United States began a criminal copyright case against Dotcom in January 2012. At Washington's request, New Zealand law enforcement officers conducted a dramatic raid on his mansion outside Auckland.
Attempts to have him sent to the United States for trial were delayed after a New Zealand court last year found that New Zealand used unlawful warrants in his arrest and illegally spied on him in the lead-up to the raid.
PRECEDENT SETTER?
Dotcom and six associates face U.S. charges that they conspired to infringe copyrights, launder money and commit racketeering and fraud.
The copyright case could set a precedent for internet liability laws and, depending on its outcome, may force entertainment companies to rethink their distribution methods.
Dotcom maintains that Megaupload, which housed everything from family photos to Hollywood blockbusters, was merely a storage facility for online files, and should not be held accountable if content stored on the site was obtained illegally.
The Justice Department counters that Megaupload encouraged piracy by paying money to users who uploaded popular content and by deleting content that was not regularly downloaded.
It said Megaupload cost copyright holders such as movie studios and record companies more than $500 million and generated more than $175 million in criminal proceeds. It called the case among the largest ever involving criminal copyright.
Dotcom launched a new file-sharing service, Mega, in January.
Many New Zealanders view Dotcom, born in Germany as Kim Schmitz, as a folk hero fighting for online freedom and willing to stand up to the U.S. and New Zealand governments.
Dotcom, who has been released on bail and is suing the New Zealand government for illegal surveillance, predicted Holder would keep a low profile during his visit.
"It's probably risk management and avoidance of bad PR because the story has not yet arrived in any big way in the U.S. media," he wrote in an email to Reuters. "Any bad coverage here might spill over to the U.S."
Holder's visit to Dotcom's country of residence is not his choice. The attorneys general of Australia, Canada, New Zealand, the United Kingdom and the United States began meeting as a quintet in 2009 to discuss legal matters including cybercrime.
After a gathering in Ottawa last year, it was New Zealand's turn to host.
(Reporting by David Ingram in Washington and Naomi Tajitsu in Wellington; Editing by Howard Goller and Xavier Briand)
Source:Reuters
joi, 2 mai 2013
Hacking Instagram Accounts using OAuth vulnerability
'Nir Goldshlager' known as Facebook hacker and founder of Break Security , who reported many critical bugs in Facebook OAuth mechanism in past few months, today disclose a critical vulnerability in Instagram Oauth that allow an attacker to hack any account. Succesful hack allows attacker to access private photos, ability to delete victim's photos and to edit comments and also the ability to post new photos. Hacker explained that there are two ways to hack Instagram accounts using OAuth, first via Hijack Instagram accounts using the Instagram OAuth or Hijack Instagram accounts using the Facebook OAuth Dialog.
Read more at: http://thehackernews.com/2013/05/hacking-instagram-accounts-using-oauth.html
Copyright © The Hacker News
Read more at: http://thehackernews.com/2013/05/hacking-instagram-accounts-using-oauth.html
Copyright © The Hacker News
Java applets run wild inside Notes
Attackers with a desire to rummage around inside the PCs of Notes users can do so merely by sending HTML emails containing a Java applet or JavaScript, IBM has admitted in a security advisory.
Full Disclosure describes the effects as potentially nasty, saying "This can be used to load arbitrary Java applets from remote sources (making it an information disclosure as well as it can be used to trigger an HTTP request once the mail is previewed/opened)"
"Combined with known Java sandbox escape vulnerabilities, it can be used to fully compromise the user reading the email," the site adds.
It's not sure just what “fully compromise” means in this context, but it is not hard to imagine the consequences of a successful attack could be unpleasant, given the Notes client links to Notes apps that in turn link to databases full of a business' important information.
Sean Richmond, a senior technology consultant at Sophos, said the ability to run Java and JavaScript in an email “could be an entry to corporate assets” and also expressed mild incredulity about the vulnerabilty. “JavaScript in email attributes is considered bad.”
Things could be worse if an applet is able to emerge from Notes into a PC's Java virtual machine, a scenario Richardson hopes won't come about because email gateways' settings should be maximally hostile to .JAR files. Of course one would also imagine an email client would be maximally hostile to HTML emails calling .JAR files.
Happily, one fix is easy: just turn off the preferences that allow Java and JavaScript to run inside Notes. Another requires tickling some .ini files.
The problem affects Notes 8.5.3 and the new Notes 9. IBM promises fixes real soon now
Source:theregister
Full Disclosure describes the effects as potentially nasty, saying "This can be used to load arbitrary Java applets from remote sources (making it an information disclosure as well as it can be used to trigger an HTTP request once the mail is previewed/opened)"
"Combined with known Java sandbox escape vulnerabilities, it can be used to fully compromise the user reading the email," the site adds.
It's not sure just what “fully compromise” means in this context, but it is not hard to imagine the consequences of a successful attack could be unpleasant, given the Notes client links to Notes apps that in turn link to databases full of a business' important information.
Sean Richmond, a senior technology consultant at Sophos, said the ability to run Java and JavaScript in an email “could be an entry to corporate assets” and also expressed mild incredulity about the vulnerabilty. “JavaScript in email attributes is considered bad.”
Things could be worse if an applet is able to emerge from Notes into a PC's Java virtual machine, a scenario Richardson hopes won't come about because email gateways' settings should be maximally hostile to .JAR files. Of course one would also imagine an email client would be maximally hostile to HTML emails calling .JAR files.
Happily, one fix is easy: just turn off the preferences that allow Java and JavaScript to run inside Notes. Another requires tickling some .ini files.
The problem affects Notes 8.5.3 and the new Notes 9. IBM promises fixes real soon now
Source:theregister
Q1 2013 Report: 973 Million Malware Emails Sent Out Each Day
Security firm Commtouch has released its Internet Threats Trend Report for the first quarter of 2013. The company reveals that, in the first three months of this year, a whopping 97.4 billion spam emails and 973 million malware emails were sent out each day.
Spam levels increased by 98% and phishing by 74% compared to December 2012. Virus outbreaks and emails carrying malware recorded an even more impressive growth – by 290% and 157%, respectively.
According to the report, the old penny stock spam, which almost completely died out, made a comeback in Q1.
As far as exploit kits go, BlackHole has once again taken center stage, being utilized in numerous cybercriminal operations.
For instance, even the massive campaigns that leveraged news about the pope and the financial crisis in Cyprus lured victims to BlackHole sites.
When it comes to spam sources, the US tops the chart, followed by Belarus, Spain, Argentina, and India.
“The dramatic rise in the quantity of unwanted and dangerous emails during the first quarter of 2013 shows that email communication is still one of the key attack vectors,” said Avi Turiel, director of threat research and market analysis at Commtouch.
"Email is still the most popular communication tool for private users and businesses alike, making it an attractive target for cybercriminals,” Turiel added.
“The rise in both emails with malware attachments and drive-by-attacks also indicates that malware distributors don't shift their focus from one attack vector to another. To the contrary, they diversify their attack methods in order to increase the efficiency of their campaigns and in order to bypass some anti-spam and antivirus measures.”
Source:Softpedia
Spam levels increased by 98% and phishing by 74% compared to December 2012. Virus outbreaks and emails carrying malware recorded an even more impressive growth – by 290% and 157%, respectively.
According to the report, the old penny stock spam, which almost completely died out, made a comeback in Q1.
As far as exploit kits go, BlackHole has once again taken center stage, being utilized in numerous cybercriminal operations.
For instance, even the massive campaigns that leveraged news about the pope and the financial crisis in Cyprus lured victims to BlackHole sites.
When it comes to spam sources, the US tops the chart, followed by Belarus, Spain, Argentina, and India.
“The dramatic rise in the quantity of unwanted and dangerous emails during the first quarter of 2013 shows that email communication is still one of the key attack vectors,” said Avi Turiel, director of threat research and market analysis at Commtouch.
"Email is still the most popular communication tool for private users and businesses alike, making it an attractive target for cybercriminals,” Turiel added.
“The rise in both emails with malware attachments and drive-by-attacks also indicates that malware distributors don't shift their focus from one attack vector to another. To the contrary, they diversify their attack methods in order to increase the efficiency of their campaigns and in order to bypass some anti-spam and antivirus measures.”
Source:Softpedia
Botnet Attack Blocker for WordPress Protects Sites Against Brute-Force Attacks
An interesting WordPress plugin released a few days ago could be of great aid to website administrators that want to make sure their sites are protected against the recent brute-force attacks.
Many websites are configured to block out an IP address after too many failed login attempts.
However, the brute-force attacks analyzed by experts rely on a botnet to crack passwords. Since each attempt to break the password can come from a different IP address, 1,000 computers are capable of trying out 5,000 combinations if the failed login attempts limit is set to 5.
This is where the Botnet Attack Blocker steps in. According to its author, the plugin ignores the different IP addresses and blocks attackers even if they use a large number of bots.
For instance, if 5 failed login attempts are set, 1,000 computers will only be allowed to try out 5 passwords, regardless of the fact that they have different IPs.
Users of Botnet Attack Blocker can select the number of allowed login attempts, the time interval between failures, and for how long to block logins. Admins can whitelist their own IP address to make sure they can access the website even during an attack.
Source:Softpedia
Many websites are configured to block out an IP address after too many failed login attempts.
However, the brute-force attacks analyzed by experts rely on a botnet to crack passwords. Since each attempt to break the password can come from a different IP address, 1,000 computers are capable of trying out 5,000 combinations if the failed login attempts limit is set to 5.
This is where the Botnet Attack Blocker steps in. According to its author, the plugin ignores the different IP addresses and blocks attackers even if they use a large number of bots.
For instance, if 5 failed login attempts are set, 1,000 computers will only be allowed to try out 5 passwords, regardless of the fact that they have different IPs.
Users of Botnet Attack Blocker can select the number of allowed login attempts, the time interval between failures, and for how long to block logins. Admins can whitelist their own IP address to make sure they can access the website even during an attack.
Source:Softpedia
Experts See Spike in Spam Emails That Use Hexadecimal URL Obfuscation
Hexadecimal URL obfuscation has been used by spammers for quite some time now because it’s a good way to bypass anti-spam filters. However, Symantec experts have recently spotted a spike in the volume of spam campaigns that use this technique.
One spam message identified by the security firm attempts to lure users to rogue pharmacy websites.
The email is simple. It’s entitled “Male pills lowest prices” and it contains the following message: “Viagra is rpeal onluy herwe (sic).”
The user can see the link to the site normally, but the source code reveals that the sender has utilized hexadecimal URL obfuscation to evade spam filters.
Source:Softpedia
Norman Helps Experts Decide If They Should Build or Buy a Malware Analysis Platform
Many IT security professionals are often required to analyze pieces of malware and determine the full extent of the damage they can cause to their organization’s networks, systems and data. The big question is: should they build their own analysis platform or buy a commercial solution?
To help professionals in taking the right decision, security firm Norman has published a new whitepaper called “The Right Testbed for the Job: Building or Buying a Malware Analysis Platform.”
The paper asks a series of questions to determine the nature of the problem, security and compliance requirements, timeframe to productive usage, knowledge transfer and key person reliance, expertise to develop the right solution, and other aspects.
Based on their answers, experts are told which decision would be best. They’re also provided a number of recommendations and tips on what must be done in each scenario.
Source:Softpedia
To help professionals in taking the right decision, security firm Norman has published a new whitepaper called “The Right Testbed for the Job: Building or Buying a Malware Analysis Platform.”
The paper asks a series of questions to determine the nature of the problem, security and compliance requirements, timeframe to productive usage, knowledge transfer and key person reliance, expertise to develop the right solution, and other aspects.
Based on their answers, experts are told which decision would be best. They’re also provided a number of recommendations and tips on what must be done in each scenario.
Source:Softpedia
Hackers accessed personal data of Reputation.com users
Reputation.com , an online reputation management website lost their own reputation when a hacker invade their website and accessed the personal data of users.
Reputation.com on Tuesday sent an email to customers disclosing the security breach. Reputation.com said in the mail that intruders had accessed the personal information including names, email , physical address, phone numbers, date of birth and occupational info.
On top of that, hackers had accessed the encrypted passwords of a small number of users. Reputation.com claimed that the passwords are highly encrypted(Hash+Salt) and "it was highly unlikely that these passwords could ever be decrypted".
One of the EHN's user commented on the issue "You fail at cryptology. The salt is stored with the hash. It doesn't add any strength to the individual hash's resistance to brute-force attacking, it only strengthens hashes from being attacked by pre-built rainbow tables. Even if you used bcrypt with a cost of 16 and 128-bit /dev/random salts, all an attacker has to do is iterate the10,000 most common passwords and they'll hit 98% of internet users. "
Source:EHacking
Apple ID Phishing Scams on the Rise, Trend Micro Experts Find
Phishing scams that target the Apple IDs of users are not uncommon, but experts from security firm Trend Micro say they’ve identified a spike in the number of websites designed to trick users into handing over their information.
After analyzing the URLs of the Apple ID phishing pages, experts noticed that they were all hosted in a folder called “~flight.” A total of 110 websites have been found hosted on a single IP address registered to an ISP in the Houston area.
The phishing sites are well designed and they target not only US users, but also people from France and the UK.
In addition, some of the scams are designed to steal more than just Apple IDs. They request victims to enter even their billing address and credit card information.
Cybercriminals lure victims to these phishing sites with bogus Apple emails which inform recipients that their accounts will expire unless they provide some information.
Experts advise users always to make sure that the site they enter their information on is secure. The URL should start with “https” and the browser should display a padlock icon in the address bar.
Source:Softpedia
Chinese Hackers Steal Info from US Defense Contractor for Several Years [Bloomberg]
Starting with 2007, at least 30 US defense contractors have been targeted by the Comment Crew, the notorious hacker collective that’s believed to be funded by the Chinese government. One of these companies was QinetiQ North America.
QinetiQ provides the US government with software used by the military, drones, robots, helicopters, satellites, weapon systems, and many other technologies that contribute to national security.
According to an extensive report from Bloomberg, the hackers targeted the company since at least 2007. Since at least 2009, it’s believed they’d been continuously operating in the organization’s networks, stealing a wide range of classified documents.
In one of the attacks, that took place in 2009, the hackers raided at least 151 machines of the firm’s Technology Solutions Group (TSG) over a 251-day period, stealing 20 gigabytes of data before being blocked.
1.3 million pages of documents, including ones containing highly sensitive military information, were stolen at the time.
In the first two and half years, it’s believed the Comment Crew – whose activities have been detailed in a recent report published by security firm Mandiant – stole over 13,000 internal passwords.
In 2010, HBGary, the security firm hacked in 2011 by Anonymous, was hired by QinetiQ along with Terremark to investigate the attacks. HBGary almost immediately identified malicious software on most of QinetiQ’s computers.
The security companies managed to clean up QinetiQ’s systems, but this only lasted for a couple of months, after which the FBI notified the contractor about another data breach.
Some say China might have already put to good use the information stolen from the firm. In April 2012, the Chinese military unveiled a bomb disposal robot that was very similar to QinetiQ’s Dragon Runner.
The technology for the Chinese robot might have been obtained from the computer of a specialist that focused on the embedded software on microchips that controlled military robots. His computer was among those infected.
Interestingly, in May 2012, QinetiQ was awarded a $4.7 million (€3.6 million) cybersecurity contract from the US Transportation Department.
Source:Bloomberg
QinetiQ provides the US government with software used by the military, drones, robots, helicopters, satellites, weapon systems, and many other technologies that contribute to national security.
According to an extensive report from Bloomberg, the hackers targeted the company since at least 2007. Since at least 2009, it’s believed they’d been continuously operating in the organization’s networks, stealing a wide range of classified documents.
In one of the attacks, that took place in 2009, the hackers raided at least 151 machines of the firm’s Technology Solutions Group (TSG) over a 251-day period, stealing 20 gigabytes of data before being blocked.
1.3 million pages of documents, including ones containing highly sensitive military information, were stolen at the time.
In the first two and half years, it’s believed the Comment Crew – whose activities have been detailed in a recent report published by security firm Mandiant – stole over 13,000 internal passwords.
In 2010, HBGary, the security firm hacked in 2011 by Anonymous, was hired by QinetiQ along with Terremark to investigate the attacks. HBGary almost immediately identified malicious software on most of QinetiQ’s computers.
The security companies managed to clean up QinetiQ’s systems, but this only lasted for a couple of months, after which the FBI notified the contractor about another data breach.
Some say China might have already put to good use the information stolen from the firm. In April 2012, the Chinese military unveiled a bomb disposal robot that was very similar to QinetiQ’s Dragon Runner.
The technology for the Chinese robot might have been obtained from the computer of a specialist that focused on the embedded software on microchips that controlled military robots. His computer was among those infected.
Interestingly, in May 2012, QinetiQ was awarded a $4.7 million (€3.6 million) cybersecurity contract from the US Transportation Department.
Source:Bloomberg
Ticket Resellers Launch DDOS Attacks Against Primary Agents to Keep Prices High
Distributed denial-of-service (DDOS) attacks are not used only by hacktivists to make a point or by cybercriminals to cover up fraud. They’re also utilized by companies for business logic attacks.
One example of such a business logic DDOS attack is revealed by Vice President and Distinguished Analyst in Gartner Research Avivah Litan.
Litan says ticket resellers in the secondary market are launching DDOS attacks against primary online ticket sellers – the companies that host the event or ones that sell tickets on their behalf at retail prices. This strategy allows resellers to keep ticket prices high.
“Ticket resellers in the secondary market want to keep the inventory on the event’s available seats low so they can keep their prices high,” the expert explained.
Source:softpedia.com
Former Obama CTO slams Twitter over lack of two-factor authentication
The chief technology officer of the Barack Obama re-election campaign has branded Twitter “ridiculous” for not offering two-factor authentication security.
Harper Reed (pictured above), who managed the technology team overseeing the president's 2012 campaign, said they regularly contacted Twitter to ask for the capability, but were ignored, for reasons that remain unclear.
“I think it’s ridiculous. It was something we constantly called and complained about but apparently they didn’t want to,” he said at an event organised by the Direct Marketing Association.
“The only thing Twitter does is monitor verified accounts so we had that but two-factor authentication is one of the most important things for email and social.”
The comments come as the demand for two-factor authentication from Twitter grows in the wake of numerous high-profile hacks on account such as Burger King, Jeep and the Associated Press.
As such, Reed urged any firm using services that have two-factor authentication capabilities, such as webmail systems or Facebook to take advantage of the protection this offers.
“If you’re a brand on Facebook or using internal or external email systems that have two-factor authentication, please turn it on,” he added.
Reed also explained that the campaign team were deeply concerned by security issues during the re-election campaign, given the rise of hacking incidents and the methods of putting information online, used by groups such as Anonymous.
“We weren’t so worried about people stealing information but about information being leaked and the embarrassment that would cause to the Obama campaign,” he said.
Source:V3
Cyber crooks dupe victims with bogus Microsoft security alerts
Webroot has detected a new wave of bogus Microsoft-themed cyber scams, looking to dupe web users with bogus security notifications.
The security firm reported detecting a number of scams targeting users with malware-laden messages masquerading as alerts from Microsoft in a blog post on Tuesday.
"Recently we have seen an increase in fake Microsoft scams, which function by tricking people into thinking that their PC is infected," wrote Webroot's Roy Tobin. He added that the cyber crooks use a variety of techniques to get the messages in front of their victims.
"There are a number of ways to figure out that this is a false alert. The first is that it's a website message and not a program; the second is that location of the website will be a random string of letters," he said.
"These websites will normally only stay active for 24-48 hours before they are pulled down. The websites' primary function is to get you to run a ‘removal tool' called ‘security cleaner'. This file is the infection and, if ran, will infect the PC and start displaying pop-ups."
The Webroot researcher said that the scams are not terribly advanced, and as long as users don't click on the malicious messages they will stay safe.
"At this stage [when the message appears], the PC is not infected so it's safe to close the browser and ignore any alerts from the website. Noting the website that displayed the message is good idea as you can notify the webmaster (if it's a legitimate website)," wrote Tobin.
Microsoft is one of many big brands used by cyber criminals to make the phishing messages look more legitimate. Last month, McAfee detected a cyber scam that used Facebook and LinkedIn to spread malware.
Source:V3
Mozilla accuses Gamma of dressing up dictators' spyware as Firefox
Firefox-maker Mozilla claims spook supplier Gamma International disguises its spyware as the popular web browser - and wants it to stop.
The non-profit software foundation slapped a cease-and-desist demand on UK-based FinFisher developer Gamma. In the legal letter, Mozilla said its Firefox trademark is being violated and that this infringement must end immediately.
Alex Fowler, the Firefox maker's director of privacy and policy, added that Mozilla takes abuse of its Firefox trademark seriously because it hurts users, creates confusion and jeopardises Mozilla’s reputation.
At the centre of the allegations is Gamma’s FinSpy program [PDF], which is deployed by cops and G-men to infiltrate a suspect's PC and allow it to be controlled from a remote server. It is claimed FinSpy masquerades as a harmless copy of the Firefox web browser so that victims who find it installed see no need to remove it.
Mozilla fired off its legal demand following the publication of a Citizen Lab report titled For Their Eyes Only: The Commercialization of Digital Spying (PDF) . See page 108 of the report for a side-by-side comparison of a legitimate install of the Mozilla browser and what the paper's authors say is a copy of FinSpy to be downloaded by the unsuspecting snoopee.
Citizen Lab is based at the Munk School of Global Affairs, at the University of Toronto, Canada, and warned of a FinFisher stealth update in March.
The surveillance software is sold by Gamma as a tool for criminal and intelligence agencies to hoover up emails, chatroom banter, Skype calls and other internet phone conversations, and to harvest a PC's hard drive for material.
'Gamma’s customers violate citizens’ human rights and online privacy'
FinSpy is part of Gamma's FinFisher suite, which El Reg was told earlier this year had been updated to evade detection and had been discovered in 25 countries.
“We cannot abide a software company using our name to disguise online surveillance tools that can be – and in several cases actually have been – used by Gamma’s customers to violate citizens’ human rights and online privacy,” Fowler said.
He stressed FinSpy does not affect Firefox. “Gamma’s software is entirely separate, and only uses our brand and trademarks to lie and mislead as one of its methods for avoiding detection and deletion,” Fowler claimed.
Gamma’s sales literature touts FinSpy as a tool for intelligence and law enforcement work - but Citizen Lab reckons citizens who are critical of the government in Bahrain and supporters of opposition candidates in Malaysia’s elections on 5 May have received emails that attempt to trick them into installing FinSpy on their Windows PCs.
Citizen Lab's writers claimed victims are unaware of what they are downloading because it comes packaged as "Firefox.exe" and sports labelling, version number, product name and copyright and trademark descriptions copies from a legit build of the open-source web browser.
Source: The Register
The non-profit software foundation slapped a cease-and-desist demand on UK-based FinFisher developer Gamma. In the legal letter, Mozilla said its Firefox trademark is being violated and that this infringement must end immediately.
Alex Fowler, the Firefox maker's director of privacy and policy, added that Mozilla takes abuse of its Firefox trademark seriously because it hurts users, creates confusion and jeopardises Mozilla’s reputation.
At the centre of the allegations is Gamma’s FinSpy program [PDF], which is deployed by cops and G-men to infiltrate a suspect's PC and allow it to be controlled from a remote server. It is claimed FinSpy masquerades as a harmless copy of the Firefox web browser so that victims who find it installed see no need to remove it.
Mozilla fired off its legal demand following the publication of a Citizen Lab report titled For Their Eyes Only: The Commercialization of Digital Spying (PDF) . See page 108 of the report for a side-by-side comparison of a legitimate install of the Mozilla browser and what the paper's authors say is a copy of FinSpy to be downloaded by the unsuspecting snoopee.
Citizen Lab is based at the Munk School of Global Affairs, at the University of Toronto, Canada, and warned of a FinFisher stealth update in March.
The surveillance software is sold by Gamma as a tool for criminal and intelligence agencies to hoover up emails, chatroom banter, Skype calls and other internet phone conversations, and to harvest a PC's hard drive for material.
'Gamma’s customers violate citizens’ human rights and online privacy'
FinSpy is part of Gamma's FinFisher suite, which El Reg was told earlier this year had been updated to evade detection and had been discovered in 25 countries.
“We cannot abide a software company using our name to disguise online surveillance tools that can be – and in several cases actually have been – used by Gamma’s customers to violate citizens’ human rights and online privacy,” Fowler said.
He stressed FinSpy does not affect Firefox. “Gamma’s software is entirely separate, and only uses our brand and trademarks to lie and mislead as one of its methods for avoiding detection and deletion,” Fowler claimed.
Gamma’s sales literature touts FinSpy as a tool for intelligence and law enforcement work - but Citizen Lab reckons citizens who are critical of the government in Bahrain and supporters of opposition candidates in Malaysia’s elections on 5 May have received emails that attempt to trick them into installing FinSpy on their Windows PCs.
Citizen Lab's writers claimed victims are unaware of what they are downloading because it comes packaged as "Firefox.exe" and sports labelling, version number, product name and copyright and trademark descriptions copies from a legit build of the open-source web browser.
Source: The Register
U.S. Department of Labor website hacked and redirecting to malicious code
During the last few hours we have identified that one the U.S. Department of Labor website has been hacked and it is serving malicious code.
Clarification:
The website affected is the The Department of Labor (DOL) Site Exposure Matrices (SEM) Website
“The Department of Labor (DOL) Site Exposure Matrices (SEM) Website is a repository of information gathered from a variety of sources regarding toxic substances present at Department of Energy (DOE) and Radiation Exposure Compensation Act (RECA) facilities covered under Part E of the Energy Employees Occupational Illness Compensation Program Act (EEOICPA)”
As you can see in the following UrlQuery report the website is including code from the malicious server dol[.]ns01[.]us:
Once you visit the website the following file is included:
www[.]sem[.]dol[.]gov/scripts/textsize.js that contains the following code:
Source:alienvault
Clarification:
The website affected is the The Department of Labor (DOL) Site Exposure Matrices (SEM) Website
“The Department of Labor (DOL) Site Exposure Matrices (SEM) Website is a repository of information gathered from a variety of sources regarding toxic substances present at Department of Energy (DOE) and Radiation Exposure Compensation Act (RECA) facilities covered under Part E of the Energy Employees Occupational Illness Compensation Program Act (EEOICPA)”
As you can see in the following UrlQuery report the website is including code from the malicious server dol[.]ns01[.]us:
Once you visit the website the following file is included:
www[.]sem[.]dol[.]gov/scripts/textsize.js that contains the following code:
Source:alienvault
Abonați-vă la:
Postări (Atom)