Se afișează postările cu eticheta Malware. Afișați toate postările
Se afișează postările cu eticheta Malware. Afișați toate postările
marți, 7 mai 2013
AutoIt scripting increasingly used by malware developers
AutoIt, a scripting language for automating Windows interface interactions, is increasingly being used by malware developers thanks to its flexibility and low learning curve, according to security researchers from Trend Micro and Bitdefender.
"Recently, we have seen an uptick in the amount of nefarious AutoIt tool code being uploaded to Pastebin," Kyle Wilhoit, a threat researcher at antivirus vendor Trend Micro, said Monday in a blog post. "One commonly seen tool, for instance, is a keylogger. Grabbing this code, anyone with bad intentions can quickly compile and run it in a matter of seconds."
"In addition to tools being found on sites like Pastebin and Pastie, we are also seeing a tremendous increase in the amount of malware utilizing AutoIt as a scripting language," Wilhoit said.
The use of AutoIt in malware development has steadily increased since 2008, Bogdan Botezatu, a senior e-threat analyst at antivirus vendor Bitdefender said Tuesday via email. The number of malware samples coded in AutoIt has recently peaked at more than 20,000 per month, he said.
"In its early days, AutoIt malware was mostly used for advertising fraud or to create self-propagation mechanisms for IM [instant messaging] worms," Botezatu said. "Nowadays, AutoIt malware ranges from ransomware to remote access applications."
One particularly sophisticated piece of AutoIt-based malware discovered recently was a version of the DarkComet RAT (remote access Trojan program), Wilhoit said. This malware opens a backdoor on the victim's machine, communicates with a remote command and control server and modifies Windows firewall policies, he said.
The DarkComet RAT has been used in targeted, APT-style, attacks in the past, including by the Syrian government to spy on political activists in the country. What's interesting about the variant found by Trend Micro is that it's written in AutoIt and has a very low antivirus detection rate.
The use of scripting languages to develop sophisticated malware is not a widespread practice, because most of these languages require an interpreter to be installed on the machine or produce very large stand-alone executable files, Botezatu said.
However, there have been exceptions. For example, the Flame cyberespionage malware used the LUA scripting language to automate some tasks without being detected by antivirus products, Botezatu said.
AutoIt is extremely intuitive and easy to use, produces compiled binaries that run out of the box on modern Windows versions and is well documented, the Bitdefender researcher said. Also, there is already a lot of malicious AutoIt code available on the Web for reuse, he said.
"Most importantly, malware created in AutoIt is extremely flexible and can be easily obfuscated, which means that a single breed of malware written in AutoIt can be repackaged and re-crafted in a number of ways to prevent detection and extend its shelf life," Botezatu said.
As scripting languages like AutoIt continue to gain popularity, more malware developers are expected to migrate toward them, Wilhoit said. "The ease of use and learning, as well as the ability to post code easily to popular dropsites make this a great opportunity for actors with nefarious intentions to propagate their tools and malware."
Source:ITworld
Man Suspected of Developing and Distributing SpyEye Malware Extradited to the US
Hamza Bendelladj of Algeria, aka “Bx1,” has been extradited from Thailand – where he was arrested earlier this year while in transit from Malaysia to Egypt – to the US. He is accused of playing a critical role in developing, marketing, distributing and controlling the notorious piece of malware known as SpyEye.
The 24-year-old is charged with one count of conspiring to commit wire fraud and bank fraud, 10 counts of wire fraud, 11 counts of computer fraud, and one count of conspiracy to commit computer fraud.
If found guilty, he could spend up to 30 years in prison for conspiracy to commit wire and bank fraud, up to 5 years for conspiracy to commit computer fraud, up to 20 years for each wire fraud count, and up to 5 or 10 years for each count of computer fraud.
In addition, he could be forced to pay fines totaling $14 million (€10.6 million).
According to the US Department of Justice, between 2009 and 2011, Bendelladj and others allegedly developed, marketed and sold versions of SpyEye to other cybercriminals.
Authorities believe that Bendelladj also operated command and control (C&C) servers for the SpyEye malware.
“No violence or coercion was used to accomplish this scheme, just a computer and an Internet connection. Bendelladj’s alleged criminal reach extended across international borders, directly into victims’ homes,” said US Attorney Sally Quillian Yates.
“In a cyber-netherworld, he allegedly commercialized the wholesale theft of financial and personal information through this virus which he sold to other cybercriminals. Cybercriminals take note; we will find you. This arrest and extradition demonstrates our determination to bring you to justice.”
FBI Special Agent in Charge Mark F. Giuliano of the Atlanta Field Office commented, “The FBI has expanded its international partnerships to allow for such extraditions of criminals who know no borders.”
He added, “The federal indictment and extradition of Bendelladj should send a very clear message to those international cyber-criminals who feel safe behind their computers in foreign lands that they are, in fact, within reach.”
Source:Softpedia
vineri, 3 mai 2013
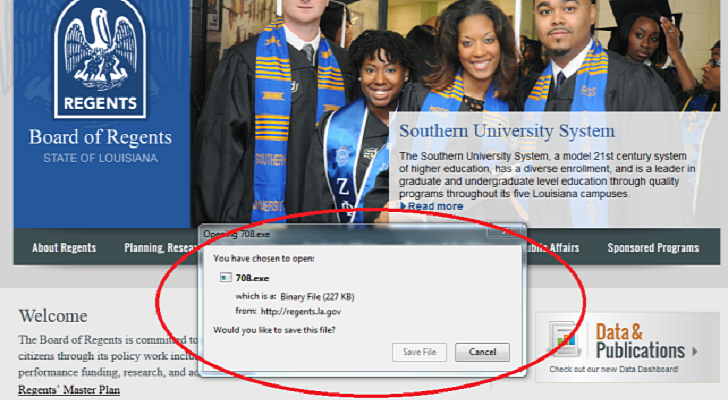
State of Louisiana Website Hacked, Spreads Sirefef Malware
The official website of the Board of Regents of the State of Louisiana (regents.la.gov) has been hacked and abused to distribute a variant of the notorious Sirefef malware.
Avast reports that the malware is hosted in the “wp-content” folder of the site and it’s served as an executable to anyone who visits a specific URL. It’s likely that the cybercriminals use spam to distribute the malicious links.
Once infected, computers become part of a peer-to-peer botnet. Such botnets are difficult to disrupt because they don’t have a main communication node that can be disconnected.
This particular botnet has already infected over 300,000 devices, but the number of infection attempts exceeds 800,000.
By compromising the websites of high-profile organizations, cybercriminals increase their campaigns’ chances of success. That’s because many users will likely click a link that appears to point to a .gov website without giving it too much thought.
I've checked the website and, unfortunately, at the time of writing, it still hosted the malware.
Additional technical details of this attack are available on Avast’s blog.
Source:Softpedia
joi, 2 mai 2013
Q1 2013 Report: 973 Million Malware Emails Sent Out Each Day
Security firm Commtouch has released its Internet Threats Trend Report for the first quarter of 2013. The company reveals that, in the first three months of this year, a whopping 97.4 billion spam emails and 973 million malware emails were sent out each day.
Spam levels increased by 98% and phishing by 74% compared to December 2012. Virus outbreaks and emails carrying malware recorded an even more impressive growth – by 290% and 157%, respectively.
According to the report, the old penny stock spam, which almost completely died out, made a comeback in Q1.
As far as exploit kits go, BlackHole has once again taken center stage, being utilized in numerous cybercriminal operations.
For instance, even the massive campaigns that leveraged news about the pope and the financial crisis in Cyprus lured victims to BlackHole sites.
When it comes to spam sources, the US tops the chart, followed by Belarus, Spain, Argentina, and India.
“The dramatic rise in the quantity of unwanted and dangerous emails during the first quarter of 2013 shows that email communication is still one of the key attack vectors,” said Avi Turiel, director of threat research and market analysis at Commtouch.
"Email is still the most popular communication tool for private users and businesses alike, making it an attractive target for cybercriminals,” Turiel added.
“The rise in both emails with malware attachments and drive-by-attacks also indicates that malware distributors don't shift their focus from one attack vector to another. To the contrary, they diversify their attack methods in order to increase the efficiency of their campaigns and in order to bypass some anti-spam and antivirus measures.”
Source:Softpedia
Spam levels increased by 98% and phishing by 74% compared to December 2012. Virus outbreaks and emails carrying malware recorded an even more impressive growth – by 290% and 157%, respectively.
According to the report, the old penny stock spam, which almost completely died out, made a comeback in Q1.
As far as exploit kits go, BlackHole has once again taken center stage, being utilized in numerous cybercriminal operations.
For instance, even the massive campaigns that leveraged news about the pope and the financial crisis in Cyprus lured victims to BlackHole sites.
When it comes to spam sources, the US tops the chart, followed by Belarus, Spain, Argentina, and India.
“The dramatic rise in the quantity of unwanted and dangerous emails during the first quarter of 2013 shows that email communication is still one of the key attack vectors,” said Avi Turiel, director of threat research and market analysis at Commtouch.
"Email is still the most popular communication tool for private users and businesses alike, making it an attractive target for cybercriminals,” Turiel added.
“The rise in both emails with malware attachments and drive-by-attacks also indicates that malware distributors don't shift their focus from one attack vector to another. To the contrary, they diversify their attack methods in order to increase the efficiency of their campaigns and in order to bypass some anti-spam and antivirus measures.”
Source:Softpedia
Norman Helps Experts Decide If They Should Build or Buy a Malware Analysis Platform
Many IT security professionals are often required to analyze pieces of malware and determine the full extent of the damage they can cause to their organization’s networks, systems and data. The big question is: should they build their own analysis platform or buy a commercial solution?
To help professionals in taking the right decision, security firm Norman has published a new whitepaper called “The Right Testbed for the Job: Building or Buying a Malware Analysis Platform.”
The paper asks a series of questions to determine the nature of the problem, security and compliance requirements, timeframe to productive usage, knowledge transfer and key person reliance, expertise to develop the right solution, and other aspects.
Based on their answers, experts are told which decision would be best. They’re also provided a number of recommendations and tips on what must be done in each scenario.
Source:Softpedia
To help professionals in taking the right decision, security firm Norman has published a new whitepaper called “The Right Testbed for the Job: Building or Buying a Malware Analysis Platform.”
The paper asks a series of questions to determine the nature of the problem, security and compliance requirements, timeframe to productive usage, knowledge transfer and key person reliance, expertise to develop the right solution, and other aspects.
Based on their answers, experts are told which decision would be best. They’re also provided a number of recommendations and tips on what must be done in each scenario.
Source:Softpedia
Abonați-vă la:
Postări (Atom)